Fill Out Your Af 4394 Form
The AF 4394 form, known as the Air Force User Agreement Statement, is a critical document for anyone accessing Department of Defense information systems. This form lays out the terms under which users can utilize U.S. Government information systems, emphasizing that access is strictly for authorized government use. Importantly, by signing the AF 4394, users consent to a range of monitoring activities that the U.S. Government may conduct, including the interception and capture of communications and data for various investigative purposes, while also ensuring that privileged communications with legal and mental health professionals remain confidential. The form specifies that the Government can inspect any data stored on its information systems, reinforcing that users should take proactive steps to identify their privileged communications. While it is made clear that the user’s acknowledgment and consent are vital, the document also sensitively addresses the need for confidentiality in matters governed by attorney-client privilege. Furthermore, it is essential for users to understand their rights and responsibilities under this agreement and to seek legal counsel if they are uncertain about any part of it. Signatures, status, and identification details are required to validate the agreement, ensuring accurate recordkeeping and compliance with legal standards.
Af 4394 Example

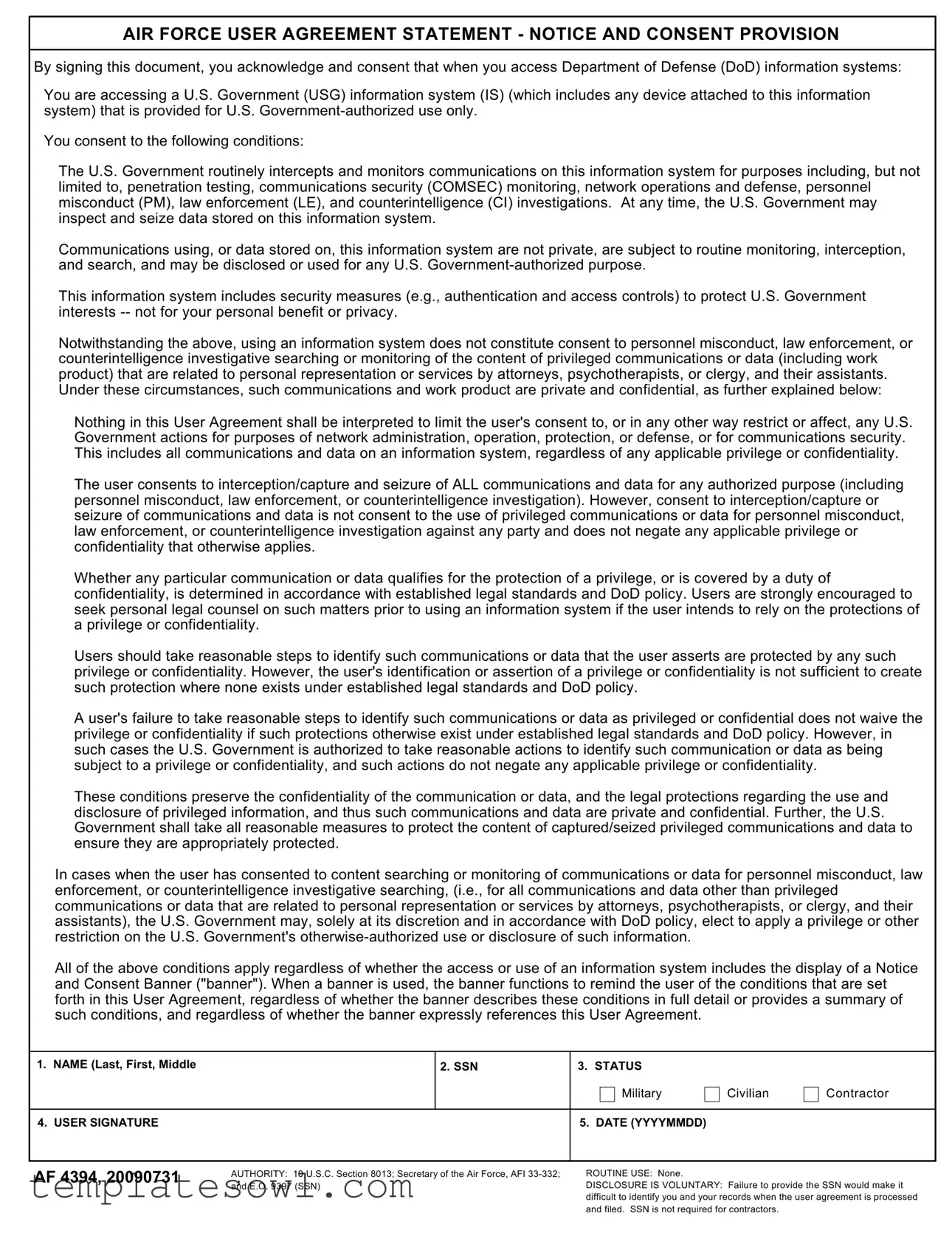
AIR FORCE USER AGREEMENT STATEMENT - NOTICE AND CONSENT PROVISION
By signing this document, you acknowledge and consent that when you access Department of Defense (DoD) information systems:
You are accessing a U.S. Government (USG) information system (IS) (which includes any device attached to this information system) that is provided for U.S.
You consent to the following conditions:
The U.S. Government routinely intercepts and monitors communications on this information system for purposes including, but not limited to, penetration testing, communications security (COMSEC) monitoring, network operations and defense, personnel misconduct (PM), law enforcement (LE), and counterintelligence (CI) investigations. At any time, the U.S. Government may inspect and seize data stored on this information system.
Communications using, or data stored on, this information system are not private, are subject to routine monitoring, interception, and search, and may be disclosed or used for any U.S.
This information system includes security measures (e.g., authentication and access controls) to protect U.S. Government interests
Notwithstanding the above, using an information system does not constitute consent to personnel misconduct, law enforcement, or counterintelligence investigative searching or monitoring of the content of privileged communications or data (including work product) that are related to personal representation or services by attorneys, psychotherapists, or clergy, and their assistants. Under these circumstances, such communications and work product are private and confidential, as further explained below:
Nothing in this User Agreement shall be interpreted to limit the user's consent to, or in any other way restrict or affect, any U.S. Government actions for purposes of network administration, operation, protection, or defense, or for communications security. This includes all communications and data on an information system, regardless of any applicable privilege or confidentiality.
The user consents to interception/capture and seizure of ALL communications and data for any authorized purpose (including personnel misconduct, law enforcement, or counterintelligence investigation). However, consent to interception/capture or seizure of communications and data is not consent to the use of privileged communications or data for personnel misconduct, law enforcement, or counterintelligence investigation against any party and does not negate any applicable privilege or confidentiality that otherwise applies.
Whether any particular communication or data qualifies for the protection of a privilege, or is covered by a duty of confidentiality, is determined in accordance with established legal standards and DoD policy. Users are strongly encouraged to seek personal legal counsel on such matters prior to using an information system if the user intends to rely on the protections of a privilege or confidentiality.
Users should take reasonable steps to identify such communications or data that the user asserts are protected by any such privilege or confidentiality. However, the user's identification or assertion of a privilege or confidentiality is not sufficient to create such protection where none exists under established legal standards and DoD policy.
A user's failure to take reasonable steps to identify such communications or data as privileged or confidential does not waive the privilege or confidentiality if such protections otherwise exist under established legal standards and DoD policy. However, in such cases the U.S. Government is authorized to take reasonable actions to identify such communication or data as being subject to a privilege or confidentiality, and such actions do not negate any applicable privilege or confidentiality.
These conditions preserve the confidentiality of the communication or data, and the legal protections regarding the use and disclosure of privileged information, and thus such communications and data are private and confidential. Further, the U.S. Government shall take all reasonable measures to protect the content of captured/seized privileged communications and data to ensure they are appropriately protected.
In cases when the user has consented to content searching or monitoring of communications or data for personnel misconduct, law enforcement, or counterintelligence investigative searching, (i.e., for all communications and data other than privileged communications or data that are related to personal representation or services by attorneys, psychotherapists, or clergy, and their assistants), the U.S. Government may, solely at its discretion and in accordance with DoD policy, elect to apply a privilege or other restriction on the U.S. Government's
All of the above conditions apply regardless of whether the access or use of an information system includes the display of a Notice and Consent Banner ("banner"). When a banner is used, the banner functions to remind the user of the conditions that are set forth in this User Agreement, regardless of whether the banner describes these conditions in full detail or provides a summary of such conditions, and regardless of whether the banner expressly references this User Agreement.
1. NAME (LAST, FIRST, MIDDLE
2. SSN
3. STATUS
Military
Civilian
Contractor
4. USER SIGNATURE
5. DATE (YYYYMMDD)
AF 4394, 20090731
AUTHORITY: 10 U.S.C. Section 8013; Secretary of the Air Force, AFI
ROUTINE USE: None.
DISCLOSURE IS VOLUNTARY: Failure to provide the SSN would make it difficult to identify you and your records when the user agreement is processed and filed. SSN is not required for contractors.
Form Characteristics
| Fact Name | Fact Description |
|---|---|
| Purpose | The AF 4394 form serves as a User Agreement for accessing Department of Defense (DoD) information systems. |
| Consent Acknowledgment | By signing the document, users consent to the monitoring and interception of their communications on the information system. |
| Monitoring Activities | The U.S. Government may monitor communications for network operations, personnel misconduct, and law enforcement purposes. |
| Inspection Rights | The U.S. Government has the authority to inspect and seize data stored on the information system at any time. |
| Privilege Limitations | Communications that are privileged, such as attorney-client communications, remain confidential but do not prevent monitoring for other purposes. |
| Legal Standards | Determination of any communication's privilege or confidentiality follows established legal standards and DoD policies. |
| User Responsibility | Users must take reasonable steps to identify communications or data that they believe are protected by privilege or confidentiality. |
| Non-Waiver Clause | A failure to identify privileged communications does not waive their protection if such protections exist under legal standards. |
| Privilege Protection | The U.S. Government will take reasonable measures to protect the confidentiality of captured privileged communications and data. |
| Disclosure of SSN | Providing a Social Security Number (SSN) is voluntary; however, not providing it could hinder the identification of records. |
Guidelines on Utilizing Af 4394
Filling out the AF 4394 form is an important process to establish your agreement with the user consent provisions for accessing Department of Defense information systems. Ensuring that all required information is accurately captured will help maintain your records properly and assist with quick identification in the future.
- Begin with your name: Write your last name, first name, and middle initial in the designated field.
- Enter your Social Security Number (SSN): Fill in your SSN in the appropriate box. If you are a contractor, you do not need to provide your SSN.
- Select your status: Indicate whether you are a military member, civilian, or contractor by checking the corresponding box.
- Provide your user signature: Sign the form to acknowledge your consent to the agreements outlined.
- Fill in the date: Enter the date in the format YYYYMMDD when you are signing the form.
After completing these steps, review the form to ensure all information is correct before submitting it as per your organization’s guidance. Proper submission will help secure your compliance with the listed user agreement conditions.
What You Should Know About This Form
What is the purpose of the AF 4394 form?
The AF 4394 form, also known as the Air Force User Agreement Statement, is designed to inform users about the conditions associated with accessing U.S. Government information systems. It outlines the user's acknowledgment and consent regarding monitoring, interception, and data usage by the U.S. Government. The form ensures that individuals are aware that their communications on the system are not private and may be subject to scrutiny for various authorized purposes, including security and investigative operations.
Who needs to sign the AF 4394 form?
What kind of information must be provided on the AF 4394 form?
The AF 4394 form requires basic identification information from the user. This includes the individual's name (last, first, middle), Social Security Number (SSN), status (military, civilian, or contractor), along with the user’s signature and the date of signing. While the SSN is encouraged for identification purposes, it is not mandatory for contractors to provide it.
What rights does the user give up by signing the AF 4394 form?
Can a user revoke their consent after signing the AF 4394 form?
Common mistakes
When filling out the AF 4394 form, people often make several common mistakes that can lead to issues with their agreements. First, there is a tendency to omit the Social Security Number (SSN). While contractors are not required to provide their SSN, military and civilian personnel must include it for proper identification. Missing this critical piece of information can delay processing and identification, which might complicate access to necessary systems.
Another frequent error is not clearly indicating the status of the applicant. The form requires users to select one of the three categories: Military, Civilian, or Contractor. Failing to mark the correct status can lead to misunderstandings about the agreement's applicability and the user’s entitlements.
Inaccurate personal details, such as spelling errors in the name field, can cause significant problems. The name should be written clearly and correctly. Misspellings may cause confusion during record retrieval and could impact legal or personnel matters. It’s crucial to double-check this information before submitting.
Users may also forget to sign the form, which is a clear mistake. The signature validates the agreement, indicating that the user understands and consents to the terms outlined in the document. Omitting a signature effectively renders the entire form invalid, requiring a redo.
Moreover, failing to provide the correct date can be problematic. The date must be written in the specified format (YYYYMMDD). If it’s not accurately filled out, confusion regarding the timeline of consent may arise, complicating future verifications.
Lastly, users might overlook the implications of the consent language within the form. There’s often a lack of understanding about the breadth of consent being provided regarding surveillance and monitoring. Taking the time to read and comprehend these sections ensures users are fully aware of the consequences of their agreement. It’s vital to be informed rather than to sign without understanding what you are consenting to.
Documents used along the form
The AF 4394 form serves as a crucial document for those accessing Department of Defense information systems. It outlines the user's consent and the terms under which they operate within these systems. To fully grasp the operational framework surrounding the AF 4394, it is important to consider other forms and documents commonly associated with it. Here is a list of such documents, each with a brief description.
- DD Form 2875: This is the System Authorization Access Request. It is used to request access to various Department of Defense information systems. Users fill out personal information and security clearance levels.
- AF Form 901: This is the Armed Forces License or Certificate of Competency. It verifies that a user is qualified to operate specific military systems or perform particular functions related to their work.
- SF 86: The Questionnaire for National Security Positions is essential for those requiring security clearance. It collects detailed information about a person’s background, including personal history, finances, and foreign contacts.
- AF Form 44: This form, also known as the Training Certification, is used to record user training related to specific systems. It ensures users are properly educated on the rights and responsibilities associated with system access.
- DoD 5250.01: This document outlines the policy for information security and the safeguarding of classified data within the Department of Defense. It serves as a guideline for users on handling sensitive information.
- AFI 33-332: The Air Force Instruction provides directives regarding the privacy and protection of personal information. It is often referenced in conjunction with the AF 4394 form for compliance purposes.
- Form I-9: The Employment Eligibility Verification form authenticates that individuals are legally permitted to work in the United States. This form is essential for compliance with immigration laws.
- SF 12: The Optional Form 12 is a Government Order for Payment of Services, commonly used in situations where employees or contractors are reimbursed for travel or other work-related expenses.
- DA Form 1687: The Organizational Authorization Memorandum officially designates individuals to access and control specific military property or information within the Department of Defense.
- AF Form 594: The Application and Authorization to Start, Stop, or Change Basic Allowance for Housing (BAH) is related to housing allowances for military personnel, often required for users transitioning duties.
Understanding these forms enhances clarity regarding the responsibilities and protocols in managing access to DoD information systems. Each document plays a unique role in ensuring security, compliance, and effective operation within a highly structured environment.
Similar forms
- AF Form 1168 - Statement of Suspect/Subject: Similar to the AF 4394, this form is used within the Air Force to document a suspect's statement. Both forms seek to ensure that individuals understand the conditions and rights involved while accessing or providing information, including the potential for monitoring.
- AF Form 3881 - Unsecured Information Reporting: This document requires users to acknowledge their responsibilities regarding sensitive information. Like the AF 4394, it emphasizes the importance of consent and awareness in interacting with governmental systems, reinforcing the ongoing nature of monitoring.
- DoD Cyber Awareness Challenge Documentation: This certification form acknowledges an individual's completion of cybersecurity training. Both the AF 4394 and this documentation highlight the responsibilities of users regarding the information systems, including their consent for monitoring.
- AF Form 2504 - Authorization to Release Medical Information: This form permits the release of personal health information and requires consent from the individual. Similarly, the AF 4394 outlines the conditions under which user data may be monitored and the circumstances around user consent.
- DD Form 2875 - System Authorization Access Request: This form allows individuals to request access to DoD systems. Like the AF 4394, it necessitates user consent and acknowledges monitoring, all while establishing the boundaries of privacy and access rights within government information systems.
Dos and Don'ts
When filling out the AF 4394 form, it's important to approach the process with care. Below is a list of recommendations to help ensure that the form is completed accurately and responsibly.
- Do review the entire form carefully. Understand what information is required and how it will be used before you begin to complete it.
- Do provide accurate information. Double-check your name, Social Security Number (SSN), and status to avoid any discrepancies.
- Do sign and date the form. Ensure that your signature is clear and the date is correctly filled out in the required format.
- Do seek legal advice if necessary. If you have concerns about confidentiality or privileged communications, consult with a legal professional before submitting the form.
- Don't rush through the form. Taking your time helps prevent mistakes that could complicate processing.
- Don't provide unnecessary personal information. Only include information that is specifically requested on the form.
By following these do's and don'ts, you can navigate the process with confidence, ensuring that your submission is both accurate and compliant with requirements.
Misconceptions
-
Misconception 1: The AF 4394 form guarantees privacy.
The AF 4394 form does not guarantee privacy. Users should understand that all communications and data accessed through the Department of Defense information systems can be monitored and intercepted by the U.S. Government.
-
Misconception 2: Signing means you consent to all types of monitoring.
While signing the form indicates consent to monitoring, it specifically excludes privileged communications related to attorneys, psychotherapists, or clergy. Users should be aware of these limitations.
-
Misconception 3: The AF 4394 allows for unlimited access to personal data.
The U.S. Government has the right to inspect and seize information for authorized purposes only. This does not mean unlimited access to personal data not related to the work being performed.
-
Misconception 4: Contractors do not need to sign the AF 4394 form.
While contractors are not required to provide a Social Security Number, they are still expected to acknowledge and understand the conditions of the AF 4394 if they access DoD information systems.
-
Misconception 5: If I don’t identify my communications as privileged, I waive my rights.
Failure to identify communications as privileged does not automatically waive those rights. The U.S. Government is authorized to identify such communications, which still preserves the protections where they apply.
-
Misconception 6: Monitoring is done only under extreme circumstances.
Monitoring is a routine practice conducted by the U.S. Government for various reasons, including security and personnel misconduct investigations, not solely for extreme cases.
-
Misconception 7: I can use any device to access the system without concern.
The AF 4394 outlines that any device used to access the DoD information systems is subject to monitoring and security measures. Users should exercise caution when connecting personal devices.
-
Misconception 8: The form is optional.
Using DoD information systems requires acknowledgment of the AF 4394. It is not optional, as access to these systems is contingent on acceptance of the conditions outlined.
-
Misconception 9: There are no consequences for violating the terms.
Violations of the terms outlined in the AF 4394 can lead to disciplinary actions. Understanding the user agreement is crucial to avoid unintended breaches and their associated consequences.
Key takeaways
When filling out and using the AF 4394 form, consider the following key takeaways:
- The AF 4394 form serves as an acknowledgment and consent document for accessing U.S. Government information systems.
- Users should be aware that communications and data may be routinely monitored and intercepted by the U.S. Government for various authorized purposes.
- Privileged communications, such as those with attorneys, psychotherapists, or clergy, are not subject to the same monitoring and may remain confidential under certain conditions.
- Providing your Social Security Number (SSN) is voluntary, but not supplying it may complicate the identification process when the user agreement is filed. Contractors are not required to provide an SSN.
Browse Other Templates
Ohio Drivers License - This form assists in tracking a young driver's progress.
Crews of Ships Are Covered by the - You may leave items 1 and 2 blank if you're filing a new claim.
Nj Real Estate Contract - Buyers must confirm their financial ability to complete the purchase.