Fill Out Your Assessment Chief Form
The Assessment Chief form is a crucial tool designed for Chief Executive Officers (CEOs) and boards of directors in the financial sector, particularly in light of the escalating threats posed by cyberattacks. This form stems from the Federal Financial Institutions Examination Council (FFIEC), which crafted the Cybersecurity Assessment Tool (Assessment) to empower institutions in evaluating their exposure to risks and measuring their readiness against these threats. By offering a structured and repeatable framework, the Assessment enables organizations to identify their specific vulnerabilities, assess their cybersecurity preparedness, and gauge whether their current controls align adequately with the risks they face. It integrates essential cybersecurity principles from the FFIEC Information Technology Examination Handbook as well as established standards from the National Institute of Standards and Technology (NIST) Cybersecurity Framework, ensuring a comprehensive approach to risk management. The Assessment consists of two key components: an Inherent Risk Profile that evaluates the risks associated with the institution’s operations and an assessment of Cybersecurity Maturity, which measures the effectiveness of existing cybersecurity controls. Through this process, management can identify necessary actions to enhance their cybersecurity strategy and ensure robust protection against evolving threats. Ultimately, the form serves not only to inform risk management practices but also to guide the strategic oversight that CEOs and boards must maintain in today's complex cyber risk landscape.
Assessment Chief Example

FFIEC Cybersecurity Assessment Tool
Overview for Chief Executive Officers and Boards of Directors
In light of the increasing volume and sophistication of cyber threats, the Federal Financial Institutions Examination Council1 (FFIEC) developed the Cybersecurity Assessment Tool (Assessment), on behalf of its members, to help institutions identify their risks and determine their cybersecurity preparedness. The Assessment provides a repeatable and measurable process for institutions to measure their cybersecurity preparedness over time. The Assessment incorporates
Benefits to the Institution
For institutions using the Assessment, management will be able to enhance their oversight and management of the institution’s cybersecurity by doing the following:
•Identifying factors contributing to and determining the institution’s overall cyber risk.
•Assessing the institution’s cybersecurity preparedness.
•Evaluating whether the institution’s cybersecurity preparedness is aligned with its risks.
•Determining risk management practices and controls that are needed or need enhancement and actions to be taken to achieve the desired state.
•Informing risk management strategies.
CEO and Board of Directors
The role of the chief executive officer (CEO), with management’s support, may include the responsibility to do the following:
•Develop a plan to conduct the Assessment.
•Lead employee efforts during the Assessment to facilitate timely responses from across the institution.
•Set the target state of cybersecurity preparedness that best aligns to the board of directors’ (board) stated (or approved) risk appetite.
•Review, approve, and support plans to address risk management and control weaknesses.
•Analyze and present results for executive oversight, including key stakeholders and the board, or an appropriate board committee.
1The FFIEC comprises the principals of the following: The Board of Governors of the Federal Reserve System, Federal Deposit Insurance Corporation, National Credit Union Administration, Office of the Comptroller of the Currency, Consumer Financial Protection Bureau, and State Liaison Committee.
2A mapping is available in Appendix B: Mapping Cybersecurity Assessment Tool to the NIST Cybersecurity Framework. NIST reviewed and provided input on the mapping to ensure consistency with Framework principles and to highlight the complementary nature of the two resources.
June 2015 |
1 |

FFIEC Cybersecurity Assessment Tool |
Overview for CEOs and Boards of Directors |
|
|
•Oversee the performance of ongoing monitoring to remain nimble and agile in addressing evolving areas of cybersecurity risk.
•Oversee changes to maintain or increase the desired cybersecurity preparedness.
The role of the board, or an appropriate board committee, may include the responsibility to do the following:
•Engage management in establishing the institution’s vision, risk appetite, and overall strategic direction.
•Approve plans to use the Assessment.
•Review management’s analysis of the Assessment results, inclusive of any reviews or opinions on the results issued by independent risk management or internal audit functions regarding those results.
•Review management’s determination of whether the institution’s cybersecurity preparedness is aligned with its risks.
•Review and approve plans to address any risk management or control weaknesses.
•Review the results of management’s ongoing monitoring of the institution’s exposure to and preparedness for cyber threats.
Assessment’s Parts and Process
The Assessment consists of two parts: Inherent Risk Profile and Cybersecurity Maturity. Upon completion of both parts, management can evaluate whether the institution’s inherent risk and preparedness are aligned.
Inherent Risk Profile
Cybersecurity inherent risk is the level of risk posed to the institution by the following:
•Technologies and Connection Types
•Delivery Channels
•Online/Mobile Products and Technology Services
•Organizational Characteristics
•External Threats
Inherent risk incorporates the type, volume, and complexity of the institution’s operations and threats directed at the institution. Inherent risk does not include mitigating controls. The Inherent Risk Profile includes descriptions of activities across risk categories with definitions for the least to most levels of inherent risk. The profile helps management determine exposure to risk that the institution’s activities, services, and products individually and collectively pose to the institution.
Least |
Minimal |
Moderate |
Significant |
Most Inherent |
Inherent Risk |
Inherent Risk |
Inherent Risk |
Inherent Risk |
Risk |
When each of the activities, services, and products are assessed, management can review the results and determine the institution’s overall inherent risk profile.
June 2015 |
2 |
 FFIEC Cybersecurity Assessment ToolOverview for CEOs and Boards of Directors
FFIEC Cybersecurity Assessment ToolOverview for CEOs and Boards of Directors
Cybersecurity Maturity
The Assessment’s second part is Cybersecurity Maturity, designed to help management measure |
|||
the institution’s level of risk and corresponding controls. The levels range from baseline to |
|||
innovative. Cybersecurity Maturity includes |
|
||
statements to determine whether an institution’s |
Innovative |
||
behaviors, practices, and processes can support |
|||
|
|||
cybersecurity preparedness within the following |
Advanced |
||
five domains: |
|||
|
|||
• |
Cyber Risk Management and Oversight |
Intermediate |
|
• Threat Intelligence and Collaboration |
|
||
• |
Cybersecurity Controls |
Evolving |
|
• |
External Dependency Management |
|
|
• Cyber Incident Management and Resilience
The domains include assessment factors and |
Baseline |
contributing components. Within each |
|
component, declarative statements describe |
|
activities supporting the assessment factor at each |
|
maturity level. Management determines which declarative statements best fit the current practices of the institution. All declarative statements in each maturity level, and previous levels, must be attained and sustained to achieve that domain’s maturity level. While management can determine the institution’s maturity level in each domain, the Assessment is not designed to identify an overall cybersecurity maturity level. The figure below provides the five domains and assessment factors.
Domain 1: Cyber |
Domain 2: Threat |
||||
Risk Management |
|
Intelligence & |
|||
|
|
& Oversight |
|
Collaboration |
|
|
|
Governance |
|
|
Threat |
|
|
|
|
Intelligence |
|
|
|
|
|
|
|
|
|
Risk |
|
|
Monitoring and |
|
|
Management |
|
|
Analyzing |
Domain 3:
Cybersecurity
Controls
Preventative
Controls
Detective
Controls
|
Domain 4: |
|
Domain 5: Cyber |
||
|
External |
|
|||
|
Incident Management |
||||
Dependency |
|||||
|
and Resilience |
||||
Management |
|
||||
|
|
|
|||
|
|
|
|
Incident |
|
|
|
|
|
||
|
Connections |
|
|
Resilience |
|
|
|
|
Planning and |
||
|
|
|
|
||
|
|
|
|
Strategy |
|
|
Relationship |
|
|
Detection, |
|
|
|
|
Response, and |
||
|
Management |
|
|
||
|
|
|
Mitigation |
||
|
|
|
|
||
Resources
Information
Sharing
Corrective
Controls
Escalation and
Reporting
Training and
Culture
June 2015 |
3 |
FFIEC Cybersecurity Assessment Tool |
Overview for CEOs and Boards of Directors |
|
|
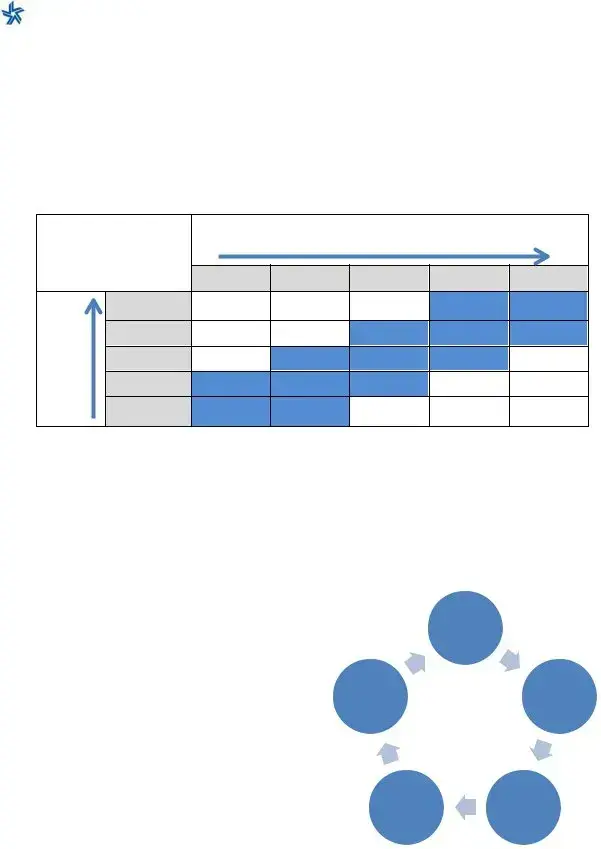
Management can review the institution’s Inherent Risk Profile in relation to its Cybersecurity Maturity results for each domain to understand whether they are aligned. The following table depicts the relationship between an institution’s Inherent Risk Profile and its domain Maturity Levels, as there is no single expected level for an institution. In general, as inherent risk rises, an institution’s maturity levels should increase. An institution’s inherent risk profile and maturity levels will change over time as threats, vulnerabilities, and operational environments change. Thus, management should consider reevaluating the institution’s inherent risk profile and cybersecurity maturity periodically and when planned changes can affect its inherent risk profile (e.g., launching new products or services, new connections).
Risk/Maturity |
Inherent Risk Levels |
|
||||
Relationship |
|
|
|
|
||
|
|
Least |
Minimal |
Moderate |
Significant |
Most |
Cybersecurity Maturity Level for |
|
Innovative |
|
|
|
|
Each Domain |
Advanced |
|
|
|
|
|
Intermediate |
|
|
|
|
||
Evolving |
|
|
|
|
||
Baseline |
|
|
|
|
||
|
|
|
|
|
|
|
Management can then decide what actions are needed either to affect the inherent risk profile or to achieve a desired state of maturity. On an ongoing basis, management may use the Assessment to identify changes to the institution’s inherent risk profile when new threats arise or when considering changes to the business strategy, such as expanding operations, offering new products and services, or entering into new
Supporting Implementation
An essential part of implementing the Assessment is to validate the institution’s process and findings and the effectiveness and sufficiency of the plans to address any identified weaknesses. The next section provides some questions to assist management and the board when using the Assessment.
Assess
maturity and inherent risk
Reevaluate |
Identify gaps |
|
in alignment |
||
|
Cybersecurity Management &
Oversight
• What are the potential cyber threats to the |
Implement |
Determine |
|
plans to |
|||
institution? |
attain and |
desired |
|
state of |
|||
sustain |
|||
|
|
||
• Is the institution a direct target of attacks? |
maturity |
maturity |
|
|
|||
|
|
•Is the institution’s cybersecurity
preparedness receiving the appropriate level of time and attention from management and the board or an appropriate board committee?
June 2015 |
4 |

FFIEC Cybersecurity Assessment Tool |
Overview for CEOs and Boards of Directors |
|
|
•Do the institution’s policies and procedures demonstrate management’s commitment to sustaining appropriate cybersecurity maturity levels?
•What is the ongoing process for gathering, monitoring, analyzing, and reporting risks?
•Who is accountable for assessing and managing the risks posed by changes to the business strategy or technology?
•Are the accountable individuals empowered with the authority to carry out these responsibilities?
•Do the inherent risk profile and cybersecurity maturity levels meet management’s business and risk management expectations? If there is misalignment, what are the proposed plans to bring them into alignment?
•How can management and the board, or an appropriate board committee, make this process part of the institution’s
Inherent Risk Profile
•What is the process for gathering and validating the information for the inherent risk profile and cybersecurity maturity?
•How can management and the board, or an appropriate board committee, support improvements to the institution’s process for conducting the Assessment?
•What do the results of the Assessment mean to the institution as it looks at its overall risk profile?
•What are the institution’s areas of highest inherent risk?
•Is management updating the institution’s inherent risk profile to reflect changes in activities, services, and products?
Cybersecurity Maturity
•How effective are the institution’s risk management activities and controls identified in the Assessment?
•Are there more efficient or effective means for attaining or improving the institution’s risk management and controls?
•What third parties does the institution rely on to support critical activities?
•What is the process to oversee third parties and understand their inherent risks and cybersecurity maturity?
•How does management validate the type and volume of attacks?
•Is the institution sharing threat information with peers, law enforcement, and critical third parties through
Summary
FFIEC has developed the Assessment to assist management and the board, or an appropriate board committee, in assessing their institution’s cybersecurity preparedness and risk. For more information and additional questions to consider, refer to the FFIEC Cybersecurity Assessment General Observations on the FFIEC’s Web site.
June 2015 |
5 |
OMB Control
Expiration Date: December 31, 2015
 FFIEC
FFIEC
Cybersecurity Assessment Tool
June 2015

FFIEC Cybersecurity Assessment Tool |
Contents |
Contents |
|
Contents |
i |
User’s Guide |
1 |
Overview |
1 |
Background |
2 |
Completing the Assessment |
2 |
Part One: Inherent Risk Profile |
3 |
Part Two: Cybersecurity Maturity |
5 |
Interpreting and Analyzing Assessment Results |
8 |
Resources |
10 |
Inherent Risk Profile |
11 |
Cybersecurity Maturity |
19 |
Domain 1: Cyber Risk Management and Oversight |
19 |
Domain 2: Threat Intelligence and Collaboration |
30 |
Domain 3: Cybersecurity Controls |
34 |
Domain 4: External Dependency Management |
47 |
Domain 5: Cyber Incident Management and Resilience |
51 |
Additional Resources
Overview for Chief Executive Officers and Boards of Directors
Appendix A: Mapping Baseline Statements to FFIEC IT Examination Handbook
Appendix B: Mapping Cybersecurity Assessment Tool to NIST Cybersecurity Framework
Appendix C: Glossary
June 2015 |
i |

FFIEC Cybersecurity Assessment Tool |
User’s Guide |
User’s Guide
Overview
In light of the increasing volume and sophistication of cyber threats, the Federal Financial Institutions Examination Council1 (FFIEC) developed the Cybersecurity Assessment Tool (Assessment), on behalf of its members, to help institutions identify their risks and determine their cybersecurity maturity.
The content of the Assessment is consistent with the principles of the FFIEC Information Technology Examination Handbook (IT Handbook) and the National Institute of Standards and Technology (NIST) Cybersecurity Framework,2 as well as industry accepted cybersecurity
practices. The Assessment provides institutions with a repeatable and measureable process to inform management of their institution’s risks and cybersecurity preparedness.
The Assessment consists of two parts: Inherent Risk Profile and Cybersecurity Maturity. The
Inherent Risk Profile identifies the institution’s inherent risk before implementing controls. The Cybersecurity Maturity includes domains, assessment factors, components, and individual
declarative statements across five maturity levels to identify specific controls and practices that are in place. While management can determine the institution’s maturity level in each domain,
the Assessment is not designed to identify an overall cybersecurity maturity level.
To complete the Assessment, management first assesses the institution’s inherent risk profile
based on five categories:
Technologies and Connection Types
Delivery Channels
Online/Mobile Products and Technology Services
Organizational Characteristics
External Threats
Management then evaluates the institution’s Cybersecurity Maturity level for each of five
domains:
Cyber Risk Management and Oversight
Threat Intelligence and Collaboration
Cybersecurity Controls
External Dependency Management
Cyber Incident Management and Resilience
1The FFIEC comprises the principals of the following: The Board of Governors of the Federal Reserve System, Federal Deposit Insurance Corporation, National Credit Union Administration, Office of the Comptroller of the Currency, Consumer Financial Protection Bureau, and State Liaison Committee.
2A mapping is available in Appendix B: Mapping Cybersecurity Assessment Tool to the NIST Cybersecurity Framework. NIST reviewed and provided input on the mapping to ensure consistency with Framework principles and to highlight the complementary nature of the two resources.
June 2015 |
1 |

FFIEC Cybersecurity Assessment Tool |
User’s Guide |
By reviewing both the institution’s inherent risk profile and maturity levels across the domains,
management can determine whether its maturity levels are appropriate in relation to its risk. If
not, the institution may take action either to reduce the level of risk or to increase the levels of maturity. This process is intended to complement, not replace, an institution’s risk management
process and cybersecurity program.
Background
The Assessment is based on the cybersecurity assessment that the FFIEC members piloted in
2014, which was designed to evaluate community institutions’ preparedness to mitigate cyber risks. NIST defines cybersecurity as “the process of protecting information by preventing, detecting, and responding to attacks.” As part of cybersecurity, institutions should consider
managing internal and external threats and vulnerabilities to protect infrastructure and information assets. The definition builds on information security as defined in FFIEC guidance.
Cyber incidents can have financial, operational, legal, and reputational impact. Recent high- profile cyber attacks demonstrate that cyber incidents can significantly affect capital and earnings. Costs may include forensic investigations, public relations campaigns, legal fees, consumer credit monitoring, and technology changes. As such, cybersecurity needs to be
integrated throughout an institution as part of
cybersecurity policies may be incorporated within the information security program. In addition, cybersecurity roles and processes referred to in the Assessment may be separate roles within the security group (or outsourced) or may be part of broader roles across the institution.
Completing the Assessment
The Assessment is designed to provide a measurable and repeatable process to assess an institution’s level of cybersecurity risk and preparedness. Part one of this Assessment is the
Inherent Risk Profile, which identifies an institution’s inherent risk relevant to cyber risks. Part two is the Cybersecurity Maturity, which determines an institution’s current state of
cybersecurity preparedness represented by maturity levels across five domains. For this Assessment to be an effective risk management tool, an institution may want to complete it periodically and as significant operational and technological changes occur.
Cyber risk programs build upon and align existing information security, business continuity, and disaster recovery programs. The Assessment is intended to be used primarily on an enterprise- wide basis and when introducing new products and services as follows:
New products, services, or initiatives. Using the Assessment before launching a new product, service, or initiative can help management understand how these might affect the institution’s inherent risk profile and resulting desired maturity levels.
June 2015 |
2 |

FFIEC Cybersecurity Assessment Tool |
User’s Guide |
Part One: Inherent Risk Profile
Part one of the Assessment identifies the institution’s inherent risk. The Inherent Risk Profile identifies activities, services, and products organized in the following categories:
Technologies and Connection Types. Certain types of connections and technologies may pose a higher inherent risk depending on the complexity and maturity, connections, and nature of the specific technology products or services. This category includes the number of Internet service provider (ISP) and
Delivery Channels. Various delivery channels for products and services may pose a higher inherent risk depending on the nature of the specific product or service offered. Inherent risk increases as the variety and number of delivery channels increases. This category addresses whether products and services are available through online and mobile delivery channels and the extent of automated teller machine (ATM) operations.
Online/Mobile Products and Technology Services. Different products and technology services offered by institutions may pose a higher inherent risk depending on the nature of the specific product or service offered. This category includes various payment services, such as debit and credit cards,
Organizational Characteristics. This category considers organizational characteristics, such as mergers and acquisitions, number of direct employees and cybersecurity contractors, changes in security staffing, the number of users with privileged access, changes in information technology (IT) environment, locations of business presence, and locations of operations and data centers.
External Threats. The volume and type of attacks (attempted or successful) affect an institution’s inherent risk exposure. This category considers the volume and sophistication of the attacks targeting the institution.
Risk Levels
Risk Levels incorporate the type, volume, and complexity of the institution’s operations and
threats directed at the institution. Inherent risk does not include mitigating controls.
June 2015 |
3 |
Form Characteristics
| Fact Name | Description |
|---|---|
| Purpose | The Assessment Chief form is designed to help institutions identify their cybersecurity risks and determine their level of preparedness against these threats. |
| Components | The Assessment consists of two main parts: Inherent Risk Profile and Cybersecurity Maturity, both of which contribute to the overall security analysis. |
| Cybersecurity Framework | The Assessment incorporates principles from the FFIEC Information Technology Examination Handbook and aligns with industry standards like the NIST Cybersecurity Framework. |
| Responsibilities | CEO and the Board of Directors are responsible for overseeing the implementation of the Assessment, including approving plans and reviewing results. |
| Regulatory Guidance | Institutions must adhere to the federal framework set forth by the Federal Financial Institutions Examination Council (FFIEC), which includes guidance from multiple regulatory bodies. |
Guidelines on Utilizing Assessment Chief
Once you have gathered the necessary information, proceed to fill out the Assessment Chief form diligently. Each section is crucial for evaluating your institution's cybersecurity preparedness and outlining the necessary steps for improvement. Ensure that all responses are accurate and reflect the current state of your organization’s cybersecurity capabilities. Follow the steps below to complete the form effectively.
- Collect Relevant Data: Gather information related to your institution's cybersecurity practices, inherent risks, and previous assessments.
- Understand the Assessment Sections: Familiarize yourself with the two main parts of the assessment: Inherent Risk Profile and Cybersecurity Maturity.
- Complete the Inherent Risk Profile: Assess each activity, service, and product according to the risk levels defined in the form. Indicate where your institution stands on the risk scale.
- Evaluate Cybersecurity Maturity: For each of the five domains, review the declarative statements and select the ones that best describe your institution's current practices and controls.
- Align Inherent Risk with Cybersecurity Maturity: Analyze whether the inherent risk profile is in agreement with the maturity levels identified in the second section.
- Document Plans for Improvement: If discrepancies exist between risk and maturity levels, outline specific plans to enhance cybersecurity practices.
- Review and Approve: Before finalizing the form, ensure that relevant stakeholders, including management and board members, review the content for accuracy.
- Submit the Form: Once all sections are filled out and reviewed, submit the form as per the provided instructions.
Completing the form is a significant step toward identifying areas of weakness and enhancing your institution's cybersecurity posture. Regular updates to this document will ensure continued alignment with evolving cybersecurity threats and the institution's risk appetite.
What You Should Know About This Form
What is the purpose of the Assessment Chief form?
The Assessment Chief form is designed to help financial institutions identify their cybersecurity risks and evaluate their preparedness against those risks. It is part of the FFIEC Cybersecurity Assessment Tool, which provides a structured process for measuring and tracking cybersecurity readiness over time. Through this form, management can understand factors contributing to their overall cyber risk and take informed steps to enhance their risk management strategies.
Who is responsible for conducting the Assessment?
The chief executive officer (CEO) plays a critical role in conducting the Assessment. With the support of management, the CEO is responsible for developing a plan, leading the execution of the Assessment, and engaging staff for timely responses. The board of directors, or an appropriate board committee, must also be involved in approving plans and reviewing the Assessment results to ensure the institution’s cybersecurity preparedness aligns with its risk appetite.
What are the two main parts of the Assessment?
The Assessment consists of two key parts: the Inherent Risk Profile and Cybersecurity Maturity. The Inherent Risk Profile evaluates the risks posed to the institution based on various factors such as technologies used, delivery channels, and external threats. Cybersecurity Maturity, on the other hand, measures the institution's current level of cybersecurity practices across five domains to determine how well these practices mitigate inherent risks.
How can institutions benefit from completing the Assessment?
Institutions can gain several benefits by utilizing the Assessment. It allows them to identify gaps in their current cybersecurity posture and determine necessary enhancements to their risk management practices. By aligning their cybersecurity preparedness with identified risks, institutions can improve overall governance and strategic oversight. Additionally, ongoing use of the Assessment enables proactive identification of evolving cyber threats and adjustments to stay ahead of potential risks.
How often should the Assessment be reevaluated?
Institutions should periodically reevaluate both their Inherent Risk Profile and Cybersecurity Maturity to ensure alignment with current risks and operational changes. This is particularly important when new products, services, or technologies are introduced, or when significant changes in the threat landscape occur. Conducting these evaluations helps institutions maintain or enhance their cybersecurity preparedness in the face of evolving challenges.
Common mistakes
Completing the Assessment Chief form is a critical task for institutions looking to bolster their cybersecurity posture. However, several common mistakes can undermine the effectiveness of this process. Understanding these errors can help ensure a thorough evaluation of cybersecurity preparedness.
One of the first mistakes is **incomplete information**. Many individuals fail to provide comprehensive details about the institution's operations, technologies, and connection types. This lack of information significantly impairs the ability to accurately assess inherent risks. Institutions should ensure that all relevant aspects are documented thoroughly to reflect their genuine operational landscape.
Another frequent error involves **misalignment between risk profiles and preparedness**. Individuals often overlook the need to correlate the institution's inherent risk profile with its cybersecurity maturity level. This oversight can lead to discrepancies that hinder strategic decision-making. To avoid this, management should regularly review and update both components to ensure they remain in harmony.
Many also neglect the crucial step of **validating their findings** during the assessment. Skipping this validation can result in inaccuracies regarding the effectiveness of existing controls. Institutions must take the time to confirm that their processes and insights accurately represent their cybersecurity landscape. Without this step, the assessment's integrity is compromised.
Additionally, there is a tendency to **avoid revisiting the assessment periodically**. Cyber threats evolve, and so do business operations. Failing to re-evaluate the inherent risk profile and cybersecurity maturity levels can leave institutions ill-prepared for new challenges. Regular assessment is essential for maintaining an up-to-date understanding of potential vulnerabilities.
A lack of **clear accountability** can further complicate the assessment process. Sometimes, roles and responsibilities regarding cybersecurity assessments are not well defined. Without clear assignments and empowerment, individuals may feel uncertain about their duties, leading to ineffective execution of the assessment process. Clarity in roles fosters a more effective and collaborative approach.
Some individuals also mistakenly assume that **cybersecurity preparedness is solely an IT concern**. This misconception can lead to inadequate involvement from key stakeholders, such as the CEO and board members. Cybersecurity should be viewed as an organization-wide priority, necessitating engagement and support from all levels of management.
Moreover, many institutions fail to **properly document changes** based on prior assessments. Each assessment should inform and guide subsequent actions. If management overlooks the necessity of recording how previous findings impacted their cybersecurity strategies, they may miss valuable opportunities for improvement.
Another common mistake is neglecting the importance of **communication and collaboration**. Organizations may silo their approach to cybersecurity, leading to disjointed efforts across departments. Open dialogue among all relevant parties is vital for developing a holistic understanding of cyber risks and crafting effective strategies to mitigate them.
Lastly, individuals often do not fully utilize the **resources available for guidance**. The FFIEC Cybersecurity Assessment Tool offers significant insights and provisions that can streamline the process. Institutions should take advantage of available documentation, training, and resources to enhance their assessment outcomes.
By recognizing and addressing these common mistakes, institutions can significantly improve their completion of the Assessment Chief form. Taking a proactive approach to these potential pitfalls will ensure a more accurate and effective evaluation of cybersecurity preparedness.
Documents used along the form
The Assessment Chief form is a crucial document for evaluating an institution's cybersecurity preparedness. However, various other forms and documents often accompany it to provide a comprehensive understanding of an institution's cybersecurity posture. Below is an overview of nine important documents that are typically utilized alongside the Assessment Chief form.
- Inherent Risk Profile Report: This report outlines the specific risks associated with the institution's operations, considering factors such as technology types, delivery channels, and organizational characteristics. It helps in identifying the institution’s exposure to cyber threats.
- Cybersecurity Maturity Assessment: This document measures the institution's current level of cybersecurity maturity across various domains. It includes evaluations across categories such as risk management, incident response, and threat intelligence.
- Risk Management Strategy Document: This strategy outlines the institution's approach to risk management, including identification, assessment, and mitigation strategies tailored to cybersecurity threats.
- Board Oversight Procedures: This document provides guidelines on how the board should oversee the institution's cybersecurity initiatives and risk management strategies, ensuring they are aligned with the institution's overall goals.
- Cyber Incident Response Plan: This plan details the steps the institution will take when a cyber incident occurs. It aims to minimize damage and outlines roles and responsibilities during a security breach.
- Employee Training Programs: Documentation of training programs designed to educate employees on cybersecurity policies, threat awareness, and best practices for reducing vulnerabilities within the organization.
- Third-Party Risk Assessment: This assessment evaluates the risks posed by third-party vendors and partners. It ensures that any external relationships do not inadvertently increase the institution's exposure to cyber threats.
- Regulatory Compliance Checklist: A checklist that ensures all cybersecurity-related policies and practices meet current regulatory requirements, helping institutions stay compliant with state and federal laws.
- Incident Log and Reporting Guidelines: This document includes procedures for logging and reporting cybersecurity incidents. It serves to maintain transparency and accountability while enabling efficient tracking of cyber events.
These documents are essential for providing a thorough understanding of cybersecurity risk management and ensuring the institution is equipped to address potential threats effectively. Assessing and utilizing these forms alongside the Assessment Chief form allows for a holistic approach to cybersecurity preparedness.
Similar forms
- Risk Assessment Framework: Similar to the Assessment Chief form, a risk assessment framework helps organizations identify, analyze, and prioritize risks. Both documents focus on understanding vulnerabilities and determining appropriate measures to mitigate risks effectively.
- Internal Audit Report: Both documents provide a structured approach to evaluating an organization’s risk management practices. Internal audit reports typically assess the adequacy of control measures, while the Assessment Chief form evaluates cybersecurity preparedness and aligns it with risk levels.
- Cybersecurity Incident Response Plan: Like the Assessment Chief form, a cybersecurity incident response plan outlines procedures for responding to threats and vulnerabilities. Each document emphasizes the importance of readiness and developing strategies to manage risks effectively.
- Business Continuity Plan: This document shares similarities with the Assessment Chief form in that both focus on preparing organizations for unexpected events. The business continuity plan aims to ensure operational resilience, while the Assessment aids in assessing and improving cybersecurity preparedness.
- Compliance Checklists: Compliance checklists serve to ensure that an organization meets regulatory requirements. The Assessment Chief form also addresses regulatory guidance and standards, ensuring that institutions are prepared to meet cybersecurity obligations.
- Strategic Risk Management Plan: Both documents provide a framework for aligning risks with organizational goals. The strategic risk management plan identifies potential threats to achieving objectives, while the Assessment Chief form helps align cybersecurity preparedness with risk levels and institutional objectives.
Dos and Don'ts
When filling out the Assessment Chief form, it's essential to follow guidelines that ensure accuracy and effectiveness. Here are ten important dos and don'ts that can guide you through the process:
- Do understand the institution’s overall cyber risk before starting.
- Do involve key stakeholders in the assessment to gather varied insights.
- Do ensure that the information gathered reflects current threats and operational environments.
- Do set clear objectives for what the assessment should accomplish.
- Do review the results with the management team and the board for comprehensive oversight.
- Don't rush through the assessment; take the necessary time for thorough evaluation.
- Don't overlook past assessment findings; they can provide valuable context.
- Don't ignore gaps in the assessment process; addressing them can strengthen cybersecurity strategies.
- Don't assume previous assumptions still hold; reassess any outdated perspectives.
- Don't keep findings solely within the cybersecurity department; share insights across the organization.
Following these dos and don'ts can enhance the effective use of the Assessment Chief form and promote better cybersecurity practices within the institution.
Misconceptions
Misconceptions about the Assessment Chief form can lead to misunderstandings regarding its purpose and implementation. Here are four common misconceptions:
- The Assessment is only for large financial institutions. This is untrue. The Assessment is designed for all financial institutions, regardless of size. Smaller institutions can benefit significantly by using the tool to identify their unique risks and improve their cybersecurity preparedness.
- The Assessment provides a single score for cybersecurity maturity. In reality, the Assessment does not assign an overall maturity score. Instead, it helps institutions evaluate their maturity across multiple domains. Each domain must be assessed individually to determine areas for improvement.
- Once completed, the Assessment is no longer needed. This misconception overlooks the need for ongoing evaluation. Cyber threats evolve, and institutions must periodically reassess their inherent risk and cybersecurity maturity to stay prepared.
- The Assessment focuses solely on technical controls. While technical controls are important, the Assessment emphasizes a comprehensive approach. This includes evaluating management practices, organizational culture, and external dependencies, ensuring a holistic view of cybersecurity preparedness.
Key takeaways
Your institution's cybersecurity preparedness is crucial in today's digital landscape. Here are key takeaways for effectively filling out and utilizing the Assessment Chief form:
- The Assessment is designed to help organizations identify risks and determine cybersecurity readiness.
- It consists of two parts: Inherent Risk Profile and Cybersecurity Maturity.
- Management must lead the Assessment, ensuring timely participation from all departments.
- The Inherent Risk Profile assesses potential threats from various factors, including technologies and organizational characteristics.
- Cybersecurity Maturity evaluates the effectiveness of existing cybersecurity controls across five domains.
- Both parts of the Assessment must be aligned to understand overall cybersecurity posture.
- The CEO plays a critical role, including developing plans and overseeing results for executive review.
- Regularly reevaluate risk profiles to stay updated on emerging threats and adjustments in business strategy.
- Management should engage the board in understanding and approving cybersecurity plans based on Assessment results.
- To address weaknesses, validate findings from the Assessment and develop actionable plans for improvement.
Utilizing the Assessment effectively will empower your organization to navigate the complex landscape of cybersecurity risks.
Browse Other Templates
Hours of Operation Template Word - The week starts fresh on Monday.
Sales and Use Tax Certificate - Taxpayers must provide their account number at the top of the form.
Baskin Robbins - List schools attended, with dates and graduation status included.
