Fill Out Your Dss 273 Form
The DSS 273 form, known as the System Access Request (SAR), plays a pivotal role in ensuring security within Department of Defense (DoD) systems. This form is essential for any individual—military, civilian, or contractor—seeking access to sensitive information managed by the DoD. Collecting crucial details such as names, Social Security Numbers, and organizational affiliations, the form serves to validate the trustworthiness of the requester. It includes sections for user type, request type, and specific applications, guiding users to provide the required information accurately. A notable feature of the DSS 273 is its dual purpose: not only does it facilitate access requests, but it also ensures adherence to privacy laws, as mandated by federal statutes like the Privacy Act. Users must navigate a series of certifications and approvals, which involve Nominating Officials and validating authorities, further emphasizing the form’s structured security protocols. Furthermore, timely submission and careful completion of the DSS 273 can significantly impact processing times, affecting the user’s access to vital systems. Hence, the form is not merely a bureaucratic necessity; it is a critical component in safeguarding national security interests.
Dss 273 Example
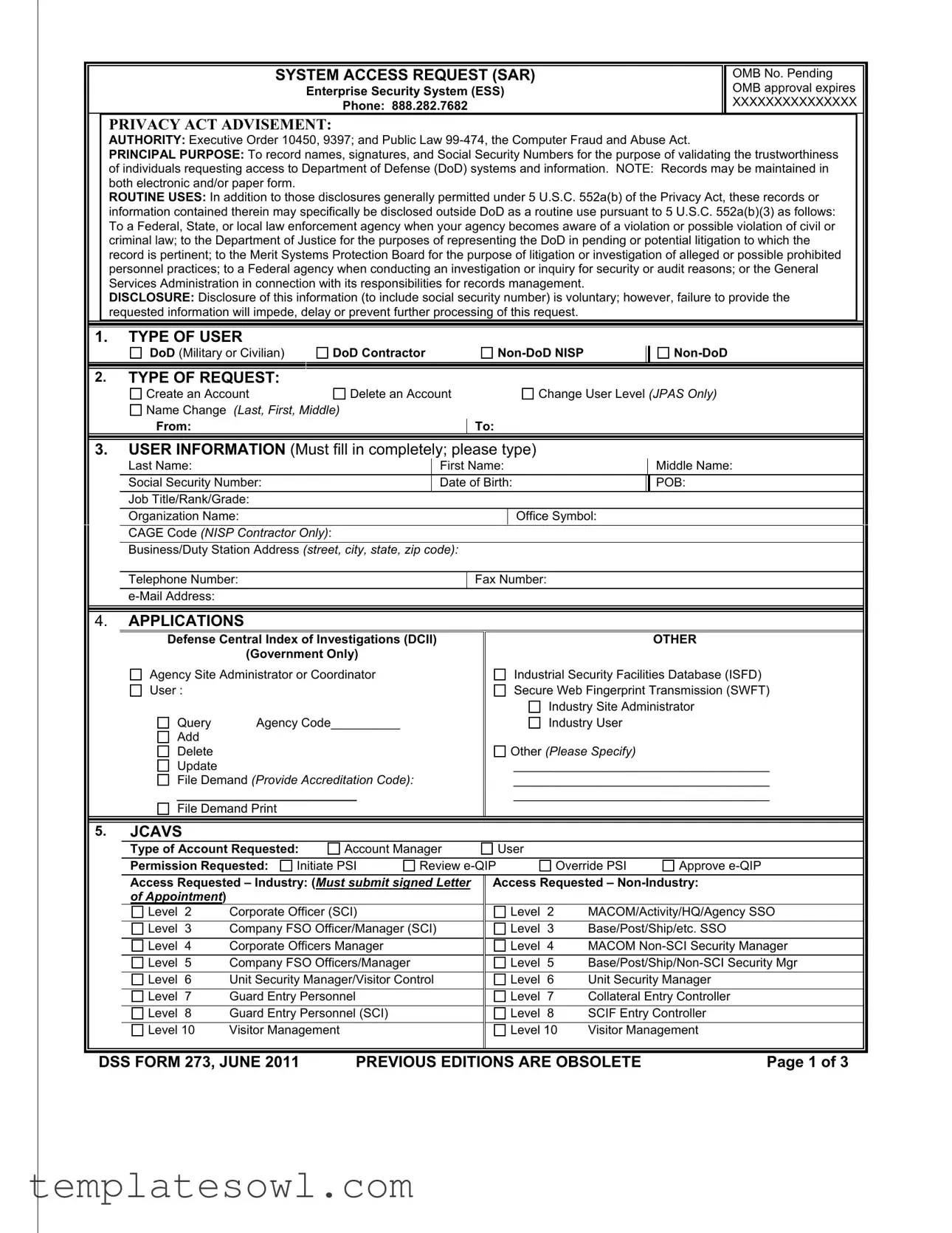
SYSTEM ACCESS REQUEST (SAR)
Enterprise Security System (ESS)
Phone: 888.282.7682
OMB No. Pending OMB approval expires
XXXXXXXXXXXXXXX
PRIVACY ACT ADVISEMENT:
AUTHORITY: Executive Order 10450, 9397; and Public Law
PRINCIPAL PURPOSE: To record names, signatures, and Social Security Numbers for the purpose of validating the trustworthiness
of individuals requesting access to Department of Defense (DoD) systems and information. NOTE: Records may be maintained in both electronic and/or paper form.
ROUTINE USES: In addition to those disclosures generally permitted under 5 U.S.C. 552a(b) of the Privacy Act, these records or information contained therein may specifically be disclosed outside DoD as a routine use pursuant to 5 U.S.C. 552a(b)(3) as follows: To a Federal, State, or local law enforcement agency when your agency becomes aware of a violation or possible violation of civil or criminal law; to the Department of Justice for the purposes of representing the DoD in pending or potential litigation to which the record is pertinent; to the Merit Systems Protection Board for the purpose of litigation or investigation of alleged or possible prohibited personnel practices; to a Federal agency when conducting an investigation or inquiry for security or audit reasons; or the General Services Administration in connection with its responsibilities for records management.
DISCLOSURE: Disclosure of this information (to include social security number) is voluntary; however, failure to provide the requested information will impede, delay or prevent further processing of this request.
1.TYPE OF USER

 DoD (Military or Civilian)
DoD (Military or Civilian)
DoD Contractor
2.TYPE OF REQUEST:
Create an Account
Name Change (Last, First, Middle)
From:
Delete an Account
To:
Change User Level (JPAS Only)
3.USER INFORMATION (Must fill in completely; please type)
Last Name: |
First Name: |
|
Middle Name: |
|
Social Security Number: |
Date of Birth: |
|
POB: |
|
|
|
|
|
|
Job Title/Rank/Grade: |
|
|
|
|
|
|
|
|
|
Organization Name: |
|
|
Office Symbol: |
|
CAGE Code (NISP Contractor Only): |
|
|
|
|
Business/Duty Station Address (street, city, state, zip code):
|
Telephone Number: |
|
Fax Number: |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
4. |
APPLICATIONS |
|
|
|
|
Defense Central Index of Investigations (DCII) |
|
OTHER |
|
|
|
(Government Only) |
|
|
|
Agency Site Administrator or Coordinator |
|
Industrial Security Facilities Database (ISFD) |
|
|
User : |
|
|
Secure Web Fingerprint Transmission (SWFT) |
|
|
|
|
Industry Site Administrator |
|
Query |
Agency Code__________ |
|
Industry User |
|
Add |
|
|
|
|
Delete |
|
|
Other (Please Specify) |
|
Update |
|
|
_____________________________________ |
|
File Demand (Provide Accreditation Code): |
|
_____________________________________ |
|
|
__________________________ |
|
_____________________________________ |
|
|
File Demand Print |
|
|
|
|
|
|
|
|
|
|
|
|
|
5. |
JCAVS |
|
|
|
Type of Account Requested:
Account Manager
User
Permission Requested:
Initiate PSI
Review
Override PSI
Approve
Access Requested – Industry: (Must submit signed Letter of Appointment)
Level |
2 |
Corporate Officer (SCI) |
|
|
|
Level 3 |
Company FSO Officer/Manager (SCI) |
|
|
|
|
Level |
4 |
Corporate Officers Manager |
|
|
|
Level 5 |
Company FSO Officers/Manager |
|
|
|
|
Level |
6 |
Unit Security Manager/Visitor Control |
|
|
|
Level |
7 |
Guard Entry Personnel |
|
|
|
Level |
8 |
Guard Entry Personnel (SCI) |
Level 10 |
Visitor Management |
|
Access Requested –
Level 2 MACOM/Activity/HQ/Agency SSO
Level 3 Base/Post/Ship/etc. SSO
Level 4 MACOM
Level 5
Level 6 Unit Security Manager
Level 7 Collateral Entry Controller
Level 8 SCIF Entry Controller
Level 10 Visitor Management
DSS FORM 273, JUNE 2011 |
PREVIOUS EDITIONS ARE OBSOLETE |
Page 1 of 3 |
User’s Last Name, First Initial: ________________________________________________
6.JAMS USER ROLES
CAF: |
CAF Team: |
Employee Code: |
Account Manager
Security Assistant
Pending User
Manager
Customer Support
Supervisor
Computer Analyst
Adjudicator
Mailroom
Case Assignment Personnel Management Support
Special Case User Can Handle:
CAF Employees
Presidential Support
Investigation Request Permissions:
Review PSQ
Approve
User Permissions:
SAP Reports
Case Management Reassign to Other CAF
SCI
JCAVS
Update Case Component
Assign/Reassign Cases
TS FOIA/PA Assign CAF Cases Reassign from Other Employee
Secret
LAA
Review Required
7. NOMINATING OFFICIAL’S CERTIFICATION (Note 1)
I certify that the above named individual meets the requirements for access and account management privileges. Furthermore, I certify that the named user requires account/access as indicated above in order to perform assigned duties.
Nominating Official’s Printed Name |
|
Nominating Official’s Signature and Date |
|
|
|
Nominating Official’s Title |
|
Nominating Official’s Telephone Number |
8. USER’S CERTIFICATION
I hereby certify that I understand that by signing this System Access Request, I am solely responsible for the use and protection of the user ID and password that I will be provided. I also understand that I am not authorized to share my user ID and password with any other individuals. I will utilize all tools and applications in accordance with the Account Management Policy and Security Policy, as well as all applicable U.S. laws and DoD regulations.
User’s Printed NameUser’s Signature and Date
9. VALIDATING OFFICIAL’S VERIFICATION (Note 2)
I have verified with the appropriate security official/manager that minimum investigative requirements for the above user have been met.
Clearance Level: ____________________________ |
Type of Investigation: _______________________________ |
Clearance Granted Date: ______________________ |
Date Investigation Completed: ________________________ |
Clearance Issued By: _________________________ |
Investigation Conducted By:__________________________ |
Printed Name of DoD Security Services Center Representative or Security Official
Signature of DoD Security Services Center Representative or Security Official, and Date
10.ADDITIONAL SAR DIRECTIVES
•The SAR must be signed by the Nominating Official and the User or it will not be processed.
•Refer to page 3 of this form and JPAS, ISFD, DCII and SWFT Frequently Asked Questions (FAQs) at https://www.dss.mil or https://www.dmdc.osd.mil/psawebdocs, for additional SAR submission procedures pertaining to the respective systems (for example, please be advised that the DSS DoD Security Services Center does not process JCAVS access requests for military personnel; these requests should be submitted to the appropriate military agency approving authority).
•SARs requiring DSS processing/approval should be submitted to the DoD Security Services Center via fax number 703.493.8965,
•The completed SAR must be maintained by the account manager for a minimum of six (6) months after the account is deleted.
Notes:
1.Nominating Official may be the Facility Security Officer, KMP, Security Manager, Information Systems Security Officer, Agency Administrator, etc. In most cases, the Nominating Official MUST be other than the User.
2.Validating Official is either a representative of the DoD Security Services Center, or if the SAR is staying within the organization, the appropriate security official. For
DSS FORM 273 (BACK), JUNE 2011 |
Page 2 of 3 |

SYSTEM ACCESS REQUEST (SAR) INSTRUCTIONS
Enterprise Security System (ESS)
SECTION |
TITLE |
INSTRUCTIONS |
|
|
|
|
|
1 |
TYPE OF USER |
Check the appropriate box for DoD (e.g., Military Branches, DoD Agencies), DoD |
|
|
|
Contractor Companies, |
|
|
|
|
|
2 |
TYPE OF REQUEST |
Check the appropriate box indicating purpose for the SAR. |
|
|
|
|
|
3 |
USER INFORMATION |
Must completely fill in. If no middle name, enter NMN. Ensure |
|
|
|
account access credentials are transmitted via |
|
|
|
|
|
4 |
APPLICATIONS |
Check the application(s) and function(s) the user requires. |
|
|
|
|
|
5 |
JCAVS |
Check appropriate boxes. See definitions below. |
|
|
|
NOTE: The appointment letter must be drafted on company letterhead, must name the |
|
|
|
Primary Account Manager and must be signed by a corporate officer (KMP). The same |
|
|
|
KMP must sign both the SAR (nominating official) and the letter. |
|
|
|
|
|
5 |
ACCOUNT MANAGER |
Account Managers will provide account maintenance on all user accounts created within |
|
|
|
their company. Responsibilities include, but are not limited to, locking/unlocking accounts, |
|
|
|
resetting passwords, logging off users, deleting accounts when no longer needed and |
|
|
|
maintaining their Security Management Offices (SMO). Account managers will create any |
|
|
|
additional accounts that are required. |
|
|
|
|
|
5 |
USER |
Depending on the level of access, users may verify clearances, update accesses, process |
|
|
|
visit notifications, and handle all other functions within JCAVS. |
|
|
|
|
|
5 |
ACCESS REQUESTED – |
Check appropriate block, using the following guidance: |
|
|
INDUSTRY |
Level 2: SCI security personnel at Corporate level, with read and write access. |
|
|
|
Level 3: SCI security personnel at echelons subordinate to Level 2 at a particular |
|
|
|
geographic location, with read and write access. |
|
|
|
Level 4: |
|
|
|
Level 5: |
|
|
|
write access. |
|
|
|
Level 6: |
|
|
|
write access. |
|
|
|
Level 7: |
|
|
|
installations, buildings, etc.), with |
|
|
|
Level 8: SCI security personnel who accomplish entry control, with |
|
|
|
Level 10: |
|
|
|
access. |
|
|
|
|
|
5 |
ACCESS REQUESTED – |
|
|
|
DoD |
|
|
|
|
|
|
N/A |
TOP OF PAGE 2 |
Ensure User’s last name and first initial are entered at the top of the page in the space |
|
|
|
provided. |
|
|
|
|
|
6 |
JAMS USER ROLES |
Provide information and check appropriate boxes for user functions, access, and |
|
|
|
permissions. JAMS is only authorized for DoD CAFs. |
|
|
|
|
|
7 |
NOMINATING OFFICIAL’S |
The Nominating Official is the individual who is authorizing that the User should have the |
|
|
CERTIFICATION |
requested accesses. The Nominating Official may be a Corporate Officer (KMP), Facility |
|
|
|
Security Officer, Security Manager, Information Systems Security Officer, Agency |
|
|
|
Administrator, etc. For JCAVS Industry Primary Account Managers, the SAR must be |
|
|
|
signed by the same KMP that signed the Appointment Letter. The Nominating |
|
|
|
Official CANNOT be the same as the User. Exceptions include the company President, |
|
|
|
for JCAVS, and the FSO, for ISFD. NOTE: SARs submitted without the Nominating |
|
|
|
Official’s signature included will not be processed. |
|
|
|
|
|
8 |
USER’S CERTIFICATION |
User must sign, acknowledging DoD/system policy. |
|
|
|
|
|
9 |
VALIDATING OFFICIAL’S |
The DoD Security Services Center (for industry only) or the Security Manager must verify |
|
|
VERIFICATION |
and indicate the following information on the following lines prior to signing: Clearance |
|
|
|
Level; Clearance Granted Date; Clearance Issued By; Type of Investigation; Date |
|
|
|
Investigation Completed; and Investigation Conducted By. For |
|
|
|
agency requests, the Chief of Security or designee must complete this section. |
|
|
|
|
|
10 |
ADDITIONAL SAR |
Provided to facilitate successful processing of the SAR. |
|
|
DIRECTIVES |
|
|
|
|
|
|
DSS FORM 273 (INSTRUCTIONS), JUNE 2011 |
Page 3 of 3 |
||
Form Characteristics
| Fact Name | Details |
|---|---|
| Purpose | The DSS Form 273 is used to record essential user information such as names, signatures, and Social Security Numbers. This helps validate the trustworthiness of individuals requesting access to Department of Defense (DoD) systems. |
| Authority | This form operates under the authority of Executive Orders 10450 and 9397, as well as Public Law 99-474, which pertains to the Computer Fraud and Abuse Act. |
| Collection of Information | Information may be maintained in both electronic and paper form, allowing flexibility in record-keeping practices. |
| Disclosure Information | While disclosure of the requested information is voluntary, failure to provide it could delay or prevent processing of the access request. |
| User Categories | Users are categorized into four types: DoD (Military or Civilian), DoD Contractors, Non-DoD NISP, and Non-DoD. |
| Processing Time | Upon submission, it typically takes at least three business days for the DoD Security Services Center to process the SAR. |
| Maintaining Records | The completed SAR must be kept by the account manager for a minimum of six months after account deletion to ensure compliance and accountability. |
Guidelines on Utilizing Dss 273
Completing the DSS 273 form can be straightforward if you follow the steps carefully. After submitting the form, the appropriate authorities will review your request, and they will notify you via email about the status of your access request. Timelines may vary, so it’s important to ensure that all sections of the form are correctly filled out for efficient processing.
- Type of User: Select the appropriate box that best fits your status—DoD (Military or Civilian), DoD Contractor, Non-DoD NISP, or Non-DoD.
- Type of Request: Check the box to indicate your purpose for filling out the form. This could be to create an account, change a name, delete an account, or change user levels.
- User Information: Complete all sections thoroughly. If you lack a middle name, write “NMN.” Double-check that your email is correct, as this is how access credentials will be sent to you.
- Applications: Indicate which applications and functions you need access to by checking the relevant boxes.
- JCAVS: Mark the appropriate checkboxes for the type of account and permission you are requesting, according to the guidance provided. Ensure that necessary letters are prepared on company letterhead when required.
- JAMS User Roles: Provide details and check boxes related to your functions and permissions if you belong to the DoD cadre.
- Nominating Official’s Certification: The Nominating Official must print their name, sign, and date the form to certify that you meet the criteria for access.
- User’s Certification: You should sign this section to acknowledge your responsibility regarding the use of your user ID and password.
- Validating Official’s Verification: A representative from the DoD Security Services Center or your own Security Manager needs to verify necessary clearance and complete the required information before signing.
- Additional SAR Directives: Ensure you have followed the guidelines provided for submitting SARs, including the necessity for all required signatures and retention of the form.
What You Should Know About This Form
What is the purpose of the DSS 273 form?
The DSS 273 form, also known as the System Access Request (SAR), is designed to collect essential information needed to validate the trustworthiness of individuals seeking access to Department of Defense (DoD) systems and information. The primary purpose includes recording names, signatures, and Social Security Numbers, ensuring that only authorized personnel can gain system access.
Who needs to complete the DSS 273 form?
Individuals affiliated with the DoD, including military personnel, civilians, and contractors, should complete the DSS 273 form. It is also applicable to non-DoD entities when they request access to specific DoD systems. Accurate completion of the form is crucial for processing the access request efficiently.
What information do I need to provide on the form?
When filling out the DSS 273 form, you must provide comprehensive personal details. These include your full name, Social Security Number, date of birth, job title or rank, organization name, and contact information, among other essentials. Ensure that you enter the information clearly and accurately since this data is pivotal for the processing of your request.
What happens if I do not provide all the requested information?
Failure to provide all requested information on the DSS 273 form can hinder the processing of your access request. Incomplete information may lead to delays or a complete denial of your application, emphasizing the importance of thoroughness and accuracy when filling out the form.
Who is required to sign the form before submission?
Before submission, the DSS 273 form must be signed by both the Nominating Official and the User. The Nominating Official authorizes the access and is typically someone like a Facility Security Officer or Security Manager. A User's signature indicates awareness of the responsibilities associated with access and system use.
How will I receive notification of my access status?
Once the DSS 273 form has been processed, notifications regarding your access status will be sent to the email address you provided on the form. It is advisable to add account.request@dsshelp.org to your email contacts to ensure that you receive the notification without any issues.
What should I do if I have additional questions about the DSS 273 form?
If you have further questions regarding the DSS 273 form or the submission process, you can visit the official websites for DSS or DMDC, where more detailed information is provided. Additionally, you can contact their help desk directly at 888.282.7682 for personalized assistance.
Common mistakes
Filling out the DSS 273 form can be a straightforward process, but there are common mistakes that people often make. One major error is failing to complete all required fields. Each section must be filled out fully, including names and social security numbers. Not providing complete information can lead to processing delays or even rejection of the request.
Another frequent oversight is incorrect user information. Individuals sometimes mix up data, such as entering the wrong social security number or misspelling names. Double-checking all entries for accuracy before submission can save time and frustration down the line.
People also often overlook the necessity of signatures. The form requires that both the Nominating Official and the User sign it. If either of these signatures is missing, the request will not be processed, leading to delays in gaining system access.
In addition, many forget to specify the appropriate Type of Request correctly. This could be anything from creating a new account to changing user levels. Selecting the wrong type can complicate the processing of the form or result in the wrong action being taken.
It’s crucial to select the right Type of User as well. Mistakes in classifying oneself or the organization can lead to serious issues, including compliance concerns. Always ensure the classification accurately reflects the user's affiliation with DoD or contractor companies.
Another common error involves misunderstanding the applications and permissions requested. The selections made in this section must align with the user’s job responsibilities and needs. Inaccurate selections can hamper operational efficiency and access to required tools.
Moreover, it’s easy to forget about the user’s certification statement. Users need to acknowledge their responsibility regarding account management. Skipping this step could show a lack of adherence to security protocols.
Lastly, failures regarding submission guidelines can lead to complications. Users often underestimate the time required for processing or forget to submit the form through the correct channels. Following the specific instructions for submission is vital for a smooth process.
Documents used along the form
The DSS 273 form is crucial for individuals seeking system access within the Department of Defense. However, it is often accompanied by various other forms and documents to ensure comprehensive processing and compliance. Below is a list of these commonly used forms, each serving its specific purpose.
- Letter of Appointment: This document is typically required for individuals seeking specific access levels within the Job Control and Access Verification System (JCAVS). It must be on company letterhead, clearly naming the Primary Account Manager and signed by a corporate officer.
- User Agreement: A user agreement outlines the requirements and responsibilities of the user regarding the use of access credentials. This document ensures that users acknowledge their understanding of the security policies in place.
- Background Investigation Authorization Form: This form is essential for obtaining necessary consent for conducting a background check on the individual requesting access. It helps validate the trustworthiness of the user.
- Privacy Act Statement: This document informs users about how their personal information will be collected, used, and disclosed. It provides transparency and ensures compliance with privacy regulations.
- CAGE Code Registration: For contractor applicants, registering for a Commercial and Government Entity (CAGE) code is often necessary. This number is unique and identifies the contractor for federal government contracts and management.
- Security Clearance Documents: These documents demonstrate that a user has the necessary security clearance for certain levels of access. This may include forms or certificates indicating the applicant's clearance level and the date granted.
Completing the DSS 273 form and submitting any associated documents promptly can significantly expedite the access approval process. This preparation is essential to adhering to the stringent security measures in place at the Department of Defense.
Similar forms
The DSS 273 form, designed for System Access Requests, shares similarities with several other important documents in the realm of security and access management. Here are four documents that are comparable to the DSS 273 form:
- SF-86 (Questionnaire for National Security Positions): Like the DSS 273, the SF-86 is crucial for validating individual trustworthiness. This form gathers comprehensive personal information necessary for the background investigation process, ensuring that applicants meet security clearance requirements.
- Form DD 2875 (System Authorization Request): The DD 2875 is used to request access to Department of Defense information systems. Similar to the DSS 273, this document requires detailed information about the requester, including their role and the level of access they seek, thereby ensuring that access is granted only to authorized individuals.
- SF-85 (Questionnaire for Non-Sensitive Positions): The SF-85 shares similarities with the DSS 273 form in that it also collects personal data for security clearance processing. Used primarily for non-sensitive positions, it helps determine the eligibility of individuals while aligning with the principles of trustworthiness and security.
- Electronic Personnel Security Questionnaire (EPSQ): The EPSQ serves as an electronic alternative to the SF-86 and SF-85, providing a streamlined format for background checks. Like the DSS 273, it is essential for evaluating an individual’s security eligibility based on the information input by the user.
Dos and Don'ts
Things You Should Do:
- Ensure all sections of the DSS 273 form are filled out completely and accurately.
- Double-check the email address provided to ensure you receive important notifications regarding your account.
- Obtain the signature of the Nominating Official before submitting the form.
- Maintain a copy of the completed form for your records for at least six months following account deletion.
Things You Shouldn't Do:
- Do not leave any mandatory fields blank, as this may delay processing.
- Avoid sharing your user ID and password with others.
- Refrain from submitting the form without the necessary signatures, as it will not be processed.
- Do not forget to add the designated email address to your contacts to ensure you receive confirmation.
Misconceptions
- Misconception 1: The DSS 273 form can be submitted without signatures.
- Misconception 2: You can submit the DSS 273 form without complete user information.
- Misconception 3: The DSS 273 form is irrelevant for contractors.
- Misconception 4: The DSS 273 form is only for new accounts.
- Misconception 5: Users can share their account information with colleagues.
- Misconception 6: The form submission process is instant.
- Misconception 7: Only certain individuals can access the DSS 273 form.
This is incorrect. Both the Nominating Official and the User must sign the form. Without these signatures, the request will not be processed.
Incomplete information will delay or prevent processing. It is essential to fill in all required fields accurately, including the Social Security Number and job title.
This is false. Contractors also need to complete the form to gain access to Department of Defense systems, just like military personnel and civilian employees.
This is misleading. The form can also be used for name changes, account deletions, and modifications to user access level.
Users are strictly prohibited from sharing their user ID and password. Each individual is responsible for the security of their account.
It is important to note that processing the DSS 273 form takes time. Allow at least three business days for processing and follow-up notifications.
This is a common misconception. The form is available for any authorized user who requires access to the DoD systems, as defined by their role.
Key takeaways
Key Takeaways for Filling Out and Using the DSS 273 Form
- The DSS 273 form is essential for individuals requesting access to Department of Defense systems and information. Ensure all sections are filled out completely and accurately.
- Disclosing your Social Security Number and other personal information is voluntary. However, not providing this information may delay or prevent processing of your request.
- A signature from both the Nominating Official and the User is mandatory for the request to be processed. Without these signatures, the form will not be accepted.
- Submission can be done via multiple channels: fax, email, or traditional mail. The processing time is generally three business days, so plan accordingly.
- Keep a copy of the completed form for at least six months after account deletion, as this is a requirement for account managers.
Browse Other Templates
California Corporation Tax Estimate,Corporate Tax Payment Form,California Estimated Tax Submission,Corporation Tax Installment Notice,Estimated Tax Payment Coupon,CA Corporation Tax Estimate 2013,Corporate Estimated Tax Schedule,Form 100-ES Payment N - Calculate and fill in the total installment amount to be paid.
Home Care Timesheet - Each time you submit a timesheet, you contribute to proper health management.