Fill Out Your Irm 15 Form
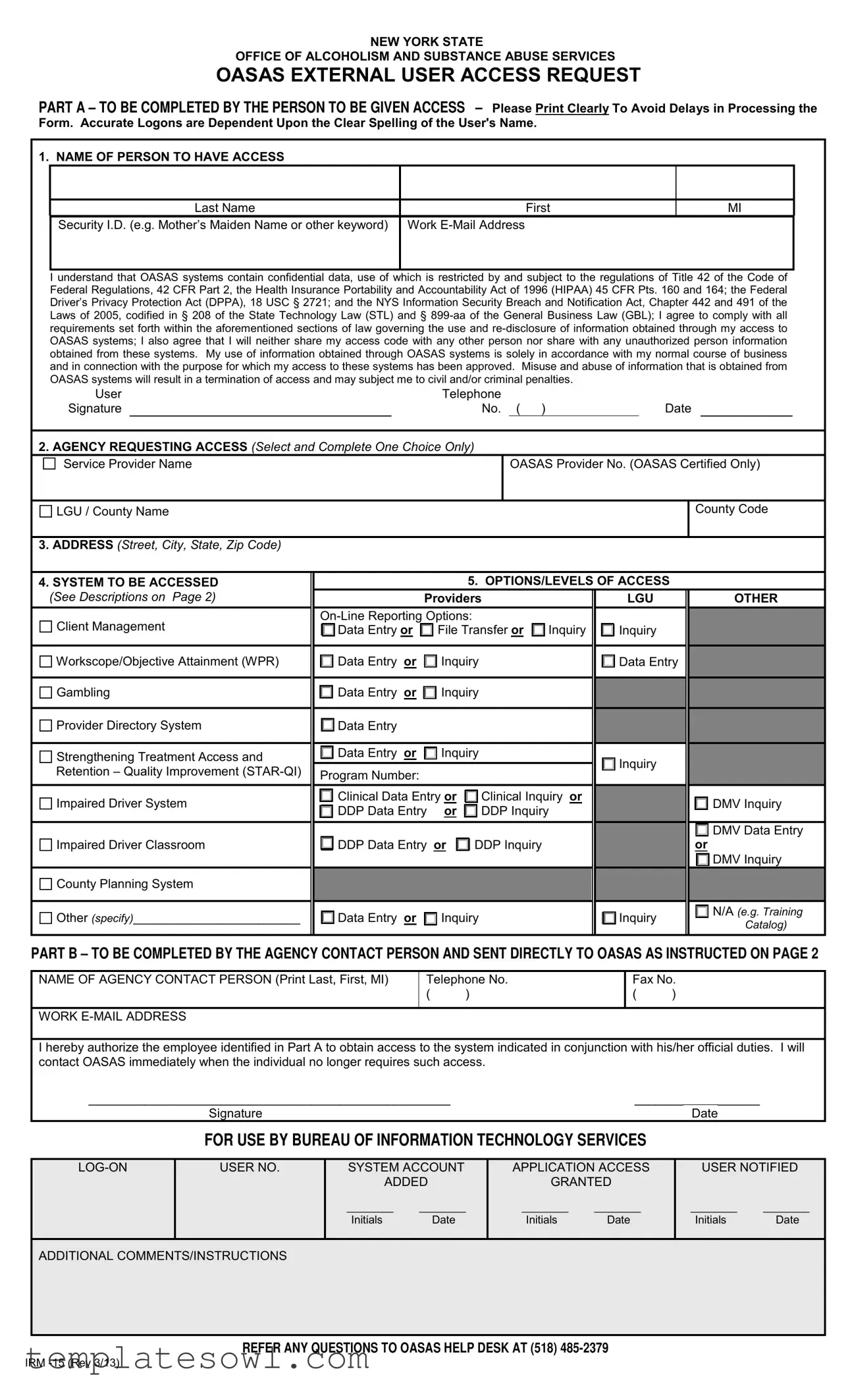
The IRM 15 form is a crucial document utilized within New York State's Office of Alcoholism and Substance Abuse Services (OASAS) to facilitate secure access to a variety of online data systems. Designed for agencies, including service providers and local governmental units, the form ensures that staff members can appropriately handle sensitive information related to alcohol and substance abuse services. The process starts with the individual requesting access filling out Part A, which captures essential information such as their name, contact details, and a security identification keyword. This helps mitigate the risks associated with unauthorized data access. Once completed, the agency contact person reviews the request in Part B to confirm it aligns with the user's official duties before directly submitting it to OASAS. The document underscores the importance of compliance with multiple federal and state privacy laws, such as HIPAA and the Federal Driver’s Privacy Protection Act, highlighting the serious implications of any misuse of the data accessed. Ultimately, the IRM 15 form streamlines the access request process while maintaining the integrity and confidentiality of vital services aimed at supporting individuals in need of assistance.
Irm 15 Example
NEW YORK STATE
OFFICE OF ALCOHOLISM AND SUBSTANCE ABUSE SERVICES
OASAS EXTERNAL USER ACCESS REQUEST
PART A – TO BE COMPLETED BY THE PERSON TO BE GIVEN ACCESS – Please Print Clearly To Avoid Delays in Processing the
Form. Accurate Logons are Dependent Upon the Clear Spelling of the User's Name.
1. NAME OF PERSON TO HAVE ACCESS
Last Name |
First |
Security I.D. (e.g. Mother’s Maiden Name or other keyword) |
Work |
|
|
MI
I understand that OASAS systems contain confidential data, use of which is restricted by and subject to the regulations of Title 42 of the Code of Federal Regulations, 42 CFR Part 2, the Health Insurance Portability and Accountability Act of 1996 (HIPAA) 45 CFR Pts. 160 and 164; the Federal Driver’s Privacy Protection Act (DPPA), 18 USC § 2721; and the NYS Information Security Breach and Notification Act, Chapter 442 and 491 of the Laws of 2005, codified in § 208 of the State Technology Law (STL) and §
User |
|
Telephone |
|
|
|
Signature |
|
No. |
( |
) |
Date |
2.AGENCY REQUESTING ACCESS (Select and Complete One Choice Only)
Service Provider Name
OASAS Provider No. (OASAS Certified Only)
LGU / County Name
3.ADDRESS (Street, City, State, Zip Code)
County Code
4. SYSTEM TO BE ACCESSED (See Descriptions on Page 2)
Client Management
Workscope/Objective Attainment (WPR)
Gambling
Provider Directory System
Strengthening Treatment Access and Retention – Quality Improvement
Impaired Driver System
Impaired Driver Classroom
County Planning System
Other (specify)________________________
5. OPTIONS/LEVELS OF ACCESS
|
Providers |
|
|
LGU |
OTHER |
||
|
|
|
|
|
|||
Data Entry or |
File Transfer or |
Inquiry |
Inquiry |
|
|||
Data Entry |
or |
Inquiry |
|
|
Data Entry |
|
|
Data Entry |
or |
Inquiry |
|
|
|
|
|
Data Entry |
|
|
|
|
|
|
|
Data Entry |
or |
Inquiry |
|
|
Inquiry |
|
|
Program Number: |
|
|
|
|
|
||
|
|
|
|
|
|
||
Clinical Data Entry or |
Clinical Inquiry |
or |
|
DMV Inquiry |
|||
DDP Data Entry |
or |
DDP Inquiry |
|
|
|||
|
|
|
|||||
|
|
|
|
|
|
|
DMV Data Entry |
DDP Data Entry or |
DDP Inquiry |
|
|
|
or |
||
|
|
|
|
|
|
|
DMV Inquiry |
Data Entry |
or |
Inquiry |
|
|
Inquiry |
N/A (e.g. Training |
|
|
|
Catalog) |
|||||
|
|
|
|
|
|
|
|
PART B – TO BE COMPLETED BY THE AGENCY CONTACT PERSON AND SENT DIRECTLY TO OASAS AS INSTRUCTED ON PAGE 2
|
NAME OF AGENCY CONTACT PERSON (Print Last, First, MI) |
Telephone No. |
Fax No. |
||
|
|
( |
) |
( |
) |
|
|
|
|
|
|
WORK
I hereby authorize the employee identified in Part A to obtain access to the system indicated in conjunction with his/her official duties. I will contact OASAS immediately when the individual no longer requires such access.
____________________________________________________ |
|
_______ |
|
______ |
|
|||||||
|
|
|
Signature |
|
|
|
|
|
|
Date |
|
|
|
|
|
FOR USE BY BUREAU OF INFORMATION TECHNOLOGY SERVICES |
|
|
|
||||||
|
|
|
|
|
|
|
|
|
||||
|
|
USER NO. |
|
SYSTEM ACCOUNT |
APPLICATION ACCESS |
|
USER NOTIFIED |
|||||
|
|
|
|
|
ADDED |
GRANTED |
|
|
|
|
||
|
|
|
|
|
________ |
________ |
________ |
________ |
|
________ |
________ |
|
|
|
|
|
|
Initials |
Date |
Initials |
Date |
|
Initials |
Date |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
ADDITIONAL COMMENTS/INSTRUCTIONS |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||
|
|
|
REFER ANY QUESTIONS TO OASAS HELP DESK AT (518) |
|
|
|
||||||
IRM |
|
|
|
|
|
|
|
|
|
|
||

INFORMATION AND INSTRUCTIONS
PURPOSE
The purpose of this form is to provide a means for agencies (services providers, Local Governmental Units [LGUs] and other authorized agencies) to arrange for their staff to obtain access to a variety of
PROCESSING THE ACCESS REQUESTS
Step 1 - The person for which access is being requested completes Part A (Sections
Department of Motor Vehicles employees who work at county DMV office locations indicate county office in the LGU / County Name, e.g. DMV Albany County. All other DMV employees enter DMV Central Office in the Service Provider Name.
The systems to be accessed (described below) should be selected, including the appropriate processing option under which data will be processed and the appropriate level of access, consistent with the tasks to be performed.
The individual signs the form agreeing that he/she will abide by the system’s users requirements.
Step 2 - The agency contact person reviews the information completed in Part A verifying that the appropriate access is being requested and completes Part B authorizing such access and providing identifying information by which they can be contacted (telephone number and email address) and mails the form directly to:
NYS OASAS
1450 Western Avenue
Albany, NY,
Attention: HELP DESK
or faxes the form to:
(518)
(please do not fax information & instruction pages)
OASAS will contact the individual directly to provide a confidential access code and instructions on establishing an individual password.
DESCRIPTIONS OF SYSTEMS TO BE ACCESSED
Client Management System - enables providers of treatment services to report client demographic and service delivery data on- line. This includes data on admissions, discharges, transfers, service delivery data, including units of service, and waiting list data. The system can accept inquiries and generate operational and statistical reports. The system is accessible by service providers and associated LGU administrators.
Workscope/Objective Attainment System - enables providers of funded treatment services to view quarterly performance data and related reports based on Workscope mandatory objective performance targets identified for various performance indices for their programs.
Gambling System – enables providers of gambling treatment services to report demographic and service delivery data
Provider Directory System – enables providers (treatment, prevention, LGU) to maintain their contact information and limited information regarding their provider and programs.
Strengthening Treatment Access and Retention – Quality Improvement
Impaired Driver System – enables providers of clinical services to impaired driving offenders and Drinking Driver Program (DDP) services to report client service delivery information
Impaired Driver Classroom – enables county DMV employees to enroll eligible motorists in New York State DDPs. Approved NYS DDPs will access the system to view rosters online, transfer or reschedule motorists to other classes as necessary, and enter information regarding instructors and class locations. Central Office DMV employees will access the system for the purpose of identifying approved DDP locations and instructors.
County Planning System – is a
SECURITY FEATURES
To assist the user in managing their password, the assignment of a “hint” is provided. The use of the “hint” allows the user to assign a new password if they have forgotten their current one. This “self management” feature is available via the Change Password link on the OASAS Applications login page.
If an incorrect login or password is used to access an OASAS system, the account will be disabled after five consecutive attempts. Access rights will only be restored by contacting the OASAS Help Desk. Please note the login and password are case sensitive.
If a user does not access an OASAS system during a consecutive 90 day period, the account will be disabled. Access rights will only be restored by contacting the OASAS Help Desk.
If a user does not access an OASAS system during a consecutive 400 day period, the account will be closed and access rights terminated. Access rights will only be restored by resubmitting a new
IRM
Form Characteristics
| Fact Name | Details |
|---|---|
| Governing Law | The IRM 15 form complies with Title 42 of the Code of Federal Regulations (CFR), HIPAA, the Federal Driver’s Privacy Protection Act, and New York State laws on information security. |
| Purpose | This form is used to grant authorized personnel access to online data systems maintained by OASAS. |
| Obtaining Access | Part A of the form must be completed by the individual requesting access, detailing their identity and agency information. |
| Confidentiality Agreement | By signing, users agree to comply with all confidentiality requirements specified in the governing laws. |
| Access Levels | Access can include options like data entry, inquiry, and reporting, based on the services being utilized. |
| Agency Authorization | Part B must be signed by the agency contact person to authorize the access request outlined in Part A. |
| Account Management | Users must manage their passwords carefully; accounts become disabled after multiple failed login attempts or inactivity. |
Guidelines on Utilizing Irm 15
Filling out the IRM 15 form is essential for obtaining access to the OASAS systems. By following these steps, you can ensure the process goes smoothly. Make sure to provide all necessary information and double-check for accuracy to avoid any delays.
- In Part A, write the Last Name, First Name, and Middle Initial of the person requesting access.
- Fill in the Security I.D., which can be a keyword like a mother’s maiden name.
- Enter a Work E-Mail Address and a Telephone Number for contact purposes.
- Complete Agency name and OASAS Provider Number, if applicable, or provide the LGU/County Name.
- Provide the full Address where the agency is located, including street, city, state, and zip code.
- Choose the system(s) to be accessed by checking the appropriate box.
- Select the Options/Levels of Access that fit your needs.
- Sign and date the form in the designated area, acknowledging the compliance requirements.
- Next, give the completed form to the Agency Contact Person.
- In Part B, the Agency Contact Person reviews the information and provides their name, phone number, fax number, and email address.
- Finally, mail the form to NYS OASAS, 1450 Western Avenue, Albany, NY, 12203-3526, or fax it to (518) 457-2387, Attention: HELP DESK.
What You Should Know About This Form
What is the purpose of the IRM-15 form?
The IRM-15 form is designed for agencies to request access to various online data systems maintained by the New York State Office of Alcoholism and Substance Abuse Services (OASAS). This access allows staff to process data related to treatment services electronically. By completing this form, agencies ensure that their employees can securely access necessary information to perform their official duties.
Who needs to complete the IRM-15 form?
The form needs to be completed by two parties: the individual requesting access (Part A) and an agency contact person (Part B). The individual fills out their personal details, including name, email, and any relevant security information. The agency contact then reviews and authorizes the request before submitting it to OASAS.
What information is required in Part A of the form?
In Part A, you must provide the person's name, security ID, work email address, and phone number. You will also select the system needed for access and outline the level of access required. Ensuring all information is accurate and complete is crucial to avoid delays in processing.
What happens after the form is submitted?
Once submitted, OASAS will reach out directly to the individual listed in Part A. They will provide a confidential access code and instructions on setting up a personal password. This step is essential for security and ensuring that only authorized users can access sensitive information.
What are the consequences of misusing information obtained through OASAS systems?
Any misuse or abuse of data obtained through OASAS systems can lead to termination of access. Furthermore, individuals may face civil and/or criminal penalties. Adhering to the regulations and guidelines provided by OASAS is vital for maintaining compliance and safeguarding confidential information.
Common mistakes
Completing the IRM 15 form can seem straightforward, but many people make common errors that delay processing. One frequent mistake is not filling in the name clearly. It's crucial to spell the first name, last name, and middle initial accurately and clearly since even a small typo can hinder access and introduce unnecessary complications.
Another misstep involves the security ID. Often, individuals overlook this section or provide vague information instead of a specific identifier. A security ID, such as a mother’s maiden name or another chosen keyword, is essential for ensuring clear and secure identification. It cannot be a mere afterthought; instead, it should be carefully selected and precisely noted.
The third common error relates to agency information. Inaccuracies about the service provider name or OASAS provider number can lead to confusion. Often, individuals either forget to include this information or mistakenly report incorrect details, which complicates the entire access request.
People also frequently misinterpret the options for levels of access. It is essential to select the appropriate systems and processing options that match the duties associated with the request. Many applicants mistakenly choose broad or incorrect categories, which may not align with their actual responsibilities and needs.
Finally, one of the biggest blunders is in the signature and date section. A missing or illegible signature can cause a request to be rejected or delayed. It's critical to ensure that the form is not only signed but also dated properly. This small detail is significant as it confirms the authenticity of the request and the awareness of the responsibilities involved in accessing sensitive data.
Documents used along the form
The IRM 15 form is a pivotal document used for granting access to various online systems maintained by the New York State Office of Alcoholism and Substance Abuse Services (OASAS). However, it is commonly accompanied by several other forms and documents that further elucidate the process or address specific needs. Below is a list of these documents, along with a brief description of each to provide a clearer understanding of their roles.
- Authorization Letter: This document serves as an official approval from an agency leader, granting permission for a staff member to access specific OASAS systems. It often includes details regarding the scope of access and the rationale behind the request.
- Confidentiality Agreement: This agreement outlines the obligations of the access requestor to safeguard the sensitive information obtained through OASAS systems. Users must acknowledge their understanding of confidentiality protocols and the repercussions of breaches.
- Access Level Documentation: This form specifies the different levels of access available for various systems and outlines what can be done with each level. Understanding these distinctions is critical for proper data management.
- OASAS User Guide: This comprehensive guide provides detailed instructions on how to navigate the OASAS systems. It serves as a reference for users to effectively utilize the systems once access is granted.
- Training Certification Document: Users may be required to complete specific training related to the systems before access is granted. This document certifies that the necessary training has been completed satisfactorily.
- Data Security Policy Acknowledgment: An acknowledgment form where users commit to following the organization’s data security policies. This policy outlines the standards expected of personnel who handle sensitive information.
- Incident Reporting Form: Should there be any breaches of data security or misuse of access, this form is utilized to report the incident. It helps ensure that any breaches are documented and addressed swiftly.
- Technical Support Request Form: Should users encounter technical difficulties while accessing the OASAS systems, this form allows them to seek assistance from technical support.
- System Access Review Document: This document outlines protocols for periodic reviews of system access privileges. Regular reviews ensure that access remains appropriate to users’ roles within the agency.
- User Feedback Form: After utilizing the OASAS systems, users can submit this form to provide feedback on their experience, helping to improve the systems for future users.
In summary, these accompanying documents are essential not just for the initial access request but also for ensuring ongoing compliance, security, and effective utilization of OASAS systems. Collectively, they help in establishing a framework where sensitive data is handled appropriately and responsibly in alignment with regulatory requirements.
Similar forms
The IRM 15 form serves a unique role in granting access to sensitive data systems related to alcoholism and substance abuse services. However, several other documents fulfill similar functions in different contexts, often centering around access authorization and data management. Below are some documents that are comparable to the IRM 15 form, along with their similarities:
- Access Request Form: Like the IRM 15, this form is used to request user access for specific systems or databases. Both require detailed information about the user and the purpose of the access.
- User Agreement Form: This document outlines the obligations and restrictions users must adhere to when accessing certain systems. Similar to the IRM 15, it includes sections for user acknowledgment and signature to confirm understanding of the rules.
- Data Sharing Agreement: Such agreements govern the sharing of confidential information between organizations. They are akin to the IRM 15 because they emphasize compliance with privacy laws and proper handling of sensitive data.
- Confidentiality Agreement: Commonly used in many organizations, this document ensures that employees understand their duty to protect sensitive information. Much like the IRM 15, it outlines the consequences of misuse.
- End User License Agreement (EULA): EULAs grant users permission to access software or systems, including restrictions on how they can use that access. This mirrors the IRM 15's focus on appropriate use of OASAS systems.
- Client Intake Form: This document collects personal information from clients seeking help. While the context is different, both documents focus on gathering essential user data for system access or service provision.
- Authorization to Release Information Form: This form is typically used to gain consent from clients for sharing their personal data. It shares similarities with the IRM 15 in its emphasis on informed consent and regulatory compliance.
- Application for User Access: Similar in purpose to the IRM 15, this form is designed to provide the necessary information to grant system access, including user details and the rationale for access.
Dos and Don'ts
When filling out the IRM 15 form, follow these guidelines to ensure a smooth process:
- Print your information clearly to avoid delays.
- Double-check the spelling of your name and security ID.
- Provide all required contact information, including a phone number and email address.
- Confirm that the agency requesting access is correctly identified.
Conversely, avoid these common mistakes:
- Do not leave any required fields blank.
- Avoid using abbreviations or nicknames for your name.
- Do not send this form without proper authorization from your agency contact person.
- Never share your access code or any confidential information with unauthorized individuals.
Misconceptions
Misconceptions about the IRM-15 form can lead to confusion and potential delays in obtaining access to crucial systems. Below are some common misunderstandings regarding this form.
- Misconception 1: The IRM-15 form can be completed haphazardly. Accuracy is critical. Illegible handwriting or unclear details can delay processing and hinder access.
- Misconception 2: Any name can be used for the security ID. The security ID must be a word or phrase known to the user, such as their mother’s maiden name. This is essential for account recovery.
- Misconception 3: Anyone can request access on behalf of another person. Only authorized agency contacts can submit Part B to authorize access, ensuring that requests are legitimate and properly vetted.
- Misconception 4: There are no consequences for misuse of the system. Misuse of information can lead to immediate termination of access and possible civil or criminal penalties. The consequences are serious and should not be taken lightly.
- Misconception 5: Completing Part A is sufficient for access. The agency contact must also complete Part B. Access won’t be granted without this essential authorization step.
- Misconception 6: Forgetting your password doesn’t have any serious implications. If you forget your password, you can use a hint to reset it. However, repeated failed login attempts can lock you out of your account.
- Misconception 7: The IRM-15 form does not require timely completion. Processing access requests can take time. Delays in submitting the form can impact your ability to access vital systems when needed.
- Misconception 8: Once you have access, it lasts indefinitely. Access will be disabled after 90 consecutive days of inactivity and terminated after 400 days. Regular use of the system is essential to maintain access.
Key takeaways
Key Takeaways for Filling Out the IRM 15 Form
- The form is divided into two parts: Part A must be completed by the individual requesting access, and Part B is for the agency contact person.
- Clear and accurate information is crucial. Double-check the spelling of names and email addresses to prevent processing delays.
- Confidentiality is paramount. Users must agree to comply with all relevant laws regarding the use of information obtained from OASAS systems.
- Selecting the appropriate system and access level is essential and should align with the user's role and responsibilities.
- Agencies must notify OASAS immediately when the individual no longer requires access to maintain security and compliance.
- Users may need to manage their login credentials carefully. If an account is inactive for a specified time, access may be terminated, requiring the resubmission of the IRM-15 form.
Browse Other Templates
Nyc-1127 Instructions 2022 - Form NYC 1127 helps determine the additional tax owed based on potential residency tax rates.
Federal Net Banking Login - Regular updates on service offerings will be communicated through the bank’s website.