Fill Out Your Qies Access Request Form
The QIES Access Request form serves as a vital tool for obtaining authorized access to sensitive data managed by the Centers for Medicare & Medicaid Services (CMS). This electronic document requires completion and subsequent submission in hard copy, featuring various request types such as new user ID creation, access modification, and user deletion. Users identify their existing CMS identifiers, alongside relevant organization details, including names, titles, and contact information. The form also categorizes requests based on user types, whether affiliated with CMS, state survey agencies, or contractors, and specifies access related to essential data reports like MDS, OASIS, and CLIA. Each request must be backed by a legitimate business need, and supervisor authorization is necessary to validate the request, which includes signatures and contact information for both the supervisor and CMS authorizers. Furthermore, users are informed of strict security requirements governing the use of CMS computer systems, ensuring the protection of sensitive information and compliance with federal guidelines. Understanding these elements is crucial for navigating the complexities of data access within a highly regulated environment.
Qies Access Request Example
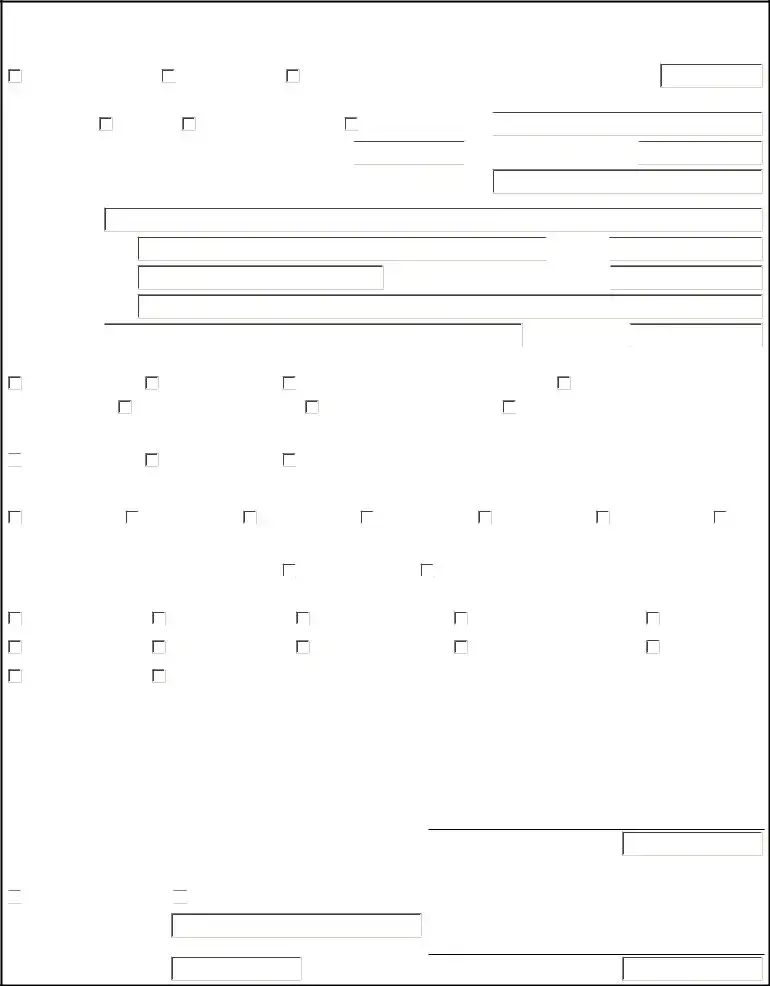
QIES National Data Access Request.
Please complete this form electronically, print, and sign hard copy to submit
Type of Request
New User ID
Change Access
Delete User ID |
Existing QIES User ID (CASPER, QW, ASPEN Web): |
Access Requested For
Type of User: |
CMS |
State Survey Agency |
Contractor |
||
DUA Number: |
|
|
|
DUA Expiration Date: |
|
|
|
|
|
||
Requester Name: |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
Last, First, Middle Initial |
|
|
Other: 
Carrier Number (MAC Only): 
Title:
Organization:
User Location: City: Work Phone Number: Work 
 State:
State:  Extension:
Extension: 
Request Date: 
CASPER Reports Access
MDS NH Reports |
MDS SB Reports |
OASIS Reports (inc. OBQI/OBQM Mgmt) |
Survey & Certification Reports |
|
CLIA MSA Report 91 |

 MDS QI
MDS QI
MDS NH Assessment
QIES Workbench Access
OBQI |
Survey and Certification (Includes Provider/Enforcement (AEM) and CLIA data) |
|
||||
The QIES Workbench data groups below contain |
|
|
||||
MDS SB |
OASIS |
LTCH |
Hospice |
ACTS |
||
Assessment |
Assessment |
Assessment |
Assessment |
Assessment |
||
|
||||||
ASPEN Web Access
CLIA |
ASSURE |
Other Access
RHHI Extract |
MDS NH Extract |
MDS 3.0 NH Viewer |
MDS Training Worksheet |
|
MDS 3.0 DMS |
MDS SB Extract |
Swing Bed Viewer |
OASIS Training Worksheet |
QTSO |
OASIS DMS |
OASIS Viewer |
|
|
|
Other access not listed: |
|
|
|
|
|
|
|
|
|
Business need for the |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
requested access: |
|
|
|
|
|
|
|
|
|
|
Supervisor Authorization - |
||
Supervisor Authorizer Name: |
|
|
|
|
|
|
|
|
Last, First, Middle Initial |
||
|
|
|
|
Supervisor Authorizer Phone: |
|
Ext: |
|
|
|
|
|
Required for Approval
Supervisor Authorizer Signature: (sign in black or blue ink)
Date:
 CMS Regional Office CMS Authorizer Name:
CMS Regional Office CMS Authorizer Name:
CMS Authorizer Phone:
CMS Authorization - Required for Approval

 CMS Central Office
CMS Central Office
CMS Authorizer Signature: (sign in black or blue ink)
Last, First, Middle Initial
Ext: |
|
Date: |
|
|
|
QIES National Data Access Request - Revised 03/31/2015

PRIVACY ACT ADVISORY STATEMENT
Privacy Act of 1974, P.L.
The information on side 1 of this form is collected and maintained under the authority of Title 5 U.S. Code, Section 552a(e)(10). This information is used for assigning, controlling, tracking and reporting authorized access to and use of CMS’s computerized information and resources. The Privacy Act prohibits disclosure of information from records protected by the stature, except in limited circumstances.
The information you furnish on this form will be maintained in the Individuals Authorized Access to the Centers for Medicare & Medicaid Services (CMS) Data Center System of Records and may be disclosed as a routine use disclosure under the routine uses established for this system as published at 59 FED. REG. 41329
SECURITY REQUIREMENTS FOR USERS OF CMS COMPUTER SYSTEMS
CMS uses computer systems that contain sensitive information to carry out its mission. Sensitive information is any information which the loss, misuse, or unauthorized access to, or modification of could adversely affect the national interest, or the conduct of Federal programs, or the privacy to which individuals are entitled under the Privacy Act. To ensure the security and privacy of sensitive information in Federal systems, the Computer Security Act of 1987 requires agencies to identify sensitive computer systems, conduct computer security training, and develop computer security plans. CMS maintains a system of records for use in assigning, controlling, tracking and reporting authorized access to and use of CMS computerized information and resources. CMS records all access to its computer systems and conducts routine reviews for unauthorized access to and/or illegal activity.
Anyone with access to CMS Computer Systems containing sensitive information must abide by the following:
-Do not disclose or lend your IDENTIFICATION NUMBER AND/OR PASSWORD to someone else. They are for your use only and will serve as your “electronic signature”. This means that you may be held responsible for the consequences of unauthorized or illegal transactions.
-Do not browse or use CMS data files for unauthorized or illegal purposes.
-Do not use CMS data files for private gain or to misrepresent yourself or CMS.
-Do not make any disclosure of CMS data that is not specifically authorized.
-Do not duplicate CMS data files, create sub files of such records, remove or transmit data unless you have been specifically authorized to do so.
-Do not change, delete, or otherwise alter CMS data files unless you have been specifically authorized to do so.
-Do not make copies of data files, with identifiable data. Or data that would allow individual identities to be deduced unless you have been specifically authorized to do so.
-Do not intentionally cause corruption or disruption of CMS data files.
A violation of these security requirements could result in termination of systems access privileges and/or disciplinary/ adverse action up to and including removal from Federal Service, depending upon the seriousness of the offense. In addition, Federal, State and/or local laws may provide criminal penalties for any person illegally accessing or using a
If you become aware of any violation of these security requirements or suspect that someone else may have used your identification number or password, immediately report that information to your security officer.
Signature of User: (sign in black or blue ink) |
Date: |
Printed User's Name:
Form Characteristics
| Fact Title | Description |
|---|---|
| Form Purpose | The QIES National Data Access Request form is used to request access to various data sources managed by CMS, facilitating improved coordination and oversight in healthcare services. |
| Type of Requests | This form allows for three types of requests: New User ID, Change Access, and Delete User ID. Clearly indicate your specific needs when completing the form. |
| Required Information | Users must provide key details, including DUA Number, expiration date, requester details, user location, and access requested for various CMS data groups. |
| Submission Process | Complete the form electronically, print it, and sign it before submission to ensure it is officially logged and processed. |
| Supervisor Authorization | Prior to form submission, it is essential to obtain supervisor authorization, including signatures and contact details. This step is crucial for approval. |
| Privacy Act Statement | The form includes a Privacy Act Advisory Statement, ensuring users understand how their information is collected and maintained per the Privacy Act of 1974. |
| Security Requirements | Users are required to adhere to strict security protocols when accessing CMS data, including safeguarding identification numbers and passwords to prevent unauthorized use. |
| Types of Access | Users can request various access options, including CASPER Reports, OASIS Reports, and more. Each type of access corresponds to specific operational needs within CMS. |
| Duration of Access | The DUA expiration date noted on the form plays a pivotal role in determining how long access will be granted. Be mindful of tracking these dates for compliance. |
| Governing Laws | The governing laws relevant to this form include the Privacy Act of 1974 and the Computer Security Act of 1987, highlighting the importance of confidentiality and security in data handling. |
Guidelines on Utilizing Qies Access Request
Filling out the QIES Access Request form is an important step in gaining access to sensitive data. Once the form is completed, it will need to be printed and signed before being submitted for processing. This ensures that your request is formally recognized and can be acted upon promptly.
- Identify the type of request: Choose whether you are requesting a new user ID, changing access, or deleting a user ID.
- Provide your existing QIES User ID: If applicable, enter your existing QIES User ID, which could be for CASPER, QW, or ASPEN Web.
- Select access requested for: Indicate the type of user (e.g., CMS, State Survey Agency, Contractor) and provide your DUA number and expiration date.
- Enter requester details: Fill in your name (last, first, middle initial), title, organization, and user location including city.
- Input contact information: Include your work phone number and work email address.
- Specify access to states: List the states to which you are requesting access, including any necessary extensions.
- Fill out request date: Enter the date you are submitting this request.
- Select access areas: Choose the specific reports and access areas you need, such as CASPER Reports, MDS NH Reports, or OASIS Reports.
- Explain your business need: Describe why you require the requested access to data.
- Provide supervisor authorization: Include the name, phone number, and signature of your supervisor along with the date.
- Include CMS authorizer information: If required, fill in the CMS authorizer's name, phone number, and signature along with the date.
- Sign the form: As the user, sign the form in black or blue ink and print your name beneath your signature.
What You Should Know About This Form
What is the purpose of the QIES Access Request form?
The QIES Access Request form is used to request access to the Quality Improvement and Evaluation System (QIES) data. This request can include creating a new user ID, changing access privileges, or deleting an existing user ID. It ensures that only authorized individuals have access to sensitive information maintained by the Centers for Medicare & Medicaid Services (CMS).
Who should fill out the QIES Access Request form?
This form should be completed by individuals who require access to CMS data systems for their work. This includes, but is not limited to, employees of state survey agencies, contractors, and other authorized personnel who need to utilize patient-level data for their duties.
What information is required when submitting the form?
When completing the form, you will need to provide various details including your name, title, organization, contact information, and the specific access you are requesting. Additionally, you will need to include your supervisor's authorization and any relevant DUA numbers and expiration dates, if applicable.
Do I need supervisor authorization for my access request?
Yes, supervisor authorization is mandatory for approval. Your supervisor must sign the form in black or blue ink. Their signature confirms that they approve your access based on the business need outlined in your request.
What types of access can be requested through this form?
The form allows for a wide range of access requests, including CASPER reports, MDS NH reports, OASIS reports, and access to the QIES Workbench, among others. Ensure you specify all necessary types of access that relate to your role and responsibilities.
How should I submit the completed form?
Once you have completed the form electronically, please print it out and sign it. The signed hard copy must then be submitted to your designated CMS representative or security officer as per your organization's submission guidelines.
What happens after I submit my request?
After submission, your request will be reviewed by the appropriate authorities at CMS. They will verify your need for access and the accuracy of the information provided on your form. If approved, you will receive instructions on how to access the QIES data systems.
What are the consequences of unauthorized access or misuse of CMS data?
Misuse of CMS data can lead to serious consequences, including termination of access privileges and disciplinary action up to removal from Federal service. There may also be legal repercussions under federal, state, and local laws for illegal access or use of government-owned systems. Always handle sensitive information responsibly.
Is there a privacy policy related to the information provided in this form?
Yes, the information collected is protected under the Privacy Act of 1974. CMS maintains this information securely and limits disclosure except under specific circumstances. By completing the form, you agree to comply with these privacy regulations to ensure the protection of sensitive data.
Common mistakes
When individuals fill out the QIES Access Request form, several common mistakes can hinder the process of obtaining access. One frequent error is failing to provide complete contact information. This includes not listing a valid work phone number or email address. Without these details, it becomes challenging for the authorizers to reach the requester, leading to delays in processing the access request.
Another mistake involves misunderstanding or misselecting the type of request. Applicants may confuse "New User ID" with "Change Access" or "Delete User ID." Such inaccuracies can result in incorrect submissions that might require rework or additional clarification. Clarity in categorizing the request is crucial for a smooth approval process.
People often overlook the importance of obtaining supervisor authorization. Many forget to secure a supervisor's signature or fail to provide the supervisor's contact information. Without this essential authorization, the request cannot be processed. Supervisors play a critical role in validating the need for access, which is why their involvement is necessary.
In some cases, individuals do not articulate the business need for the requested access clearly. A vague response can lead to misunderstandings about the request's purpose. It is essential to be specific when detailing how the access will be utilized within the organization. This specificity aids in the justification of the request.
Lastly, individuals frequently neglect to sign and date the form properly. A missing or incorrect signature can delay the processing of the request significantly. Each signature serves as an affirmation of the accuracy of the information provided, thus ensuring that all parties are accountable for their roles in the access request process.
Documents used along the form
The QIES Access Request Form is critical for any individual seeking to gain authorized access to sensitive CMS data. However, there are several other documents often required alongside this form that help ensure compliance and proper authorization. Below are some key forms that may accompany the QIES Access Request Form:
- Supervisor Authorization Form: This document requires the approval of a supervisor before access can be granted. It verifies that the workplace manager is aware of and endorses the access request.
- CMS User Agreement: This is a binding agreement that outlines the responsibilities of users when accessing sensitive data. It ensures users understand their obligations regarding data security and appropriate conduct.
- Privacy Training Certificate: Users often need to complete a privacy training course to demonstrate their understanding of data protection rules and regulations. A certificate of completion may be required for approval.
- Data Use Agreement (DUA): This formal agreement specifies how data can be used, shared, and handled by the user. It provides legal accountability for the utilization of sensitive information.
- Access Control Policy: This policy outlines the standards and procedures for accessing CMS systems. It ensures that only authorized personnel can obtain sensitive data, safeguarding against unauthorized access.
- Incident Reporting Form: In case of any data breach or unauthorized use, this form must be completed to document the incident. Prompt reporting is vital for mitigating risks and enhances security protocols.
- IT Security Policy Acknowledgment: Users typically need to acknowledge receipt and understanding of the organization's IT security policies. This affirmation helps reinforce the importance of protecting sensitive information.
Understanding the purpose and necessity of these documents can significantly streamline the access request process and ensure compliance with federal regulations. Be proactive in preparing these materials as delays in submission can impact operational efficiency. Make sure all required documentation is complete and accurate to avoid any potential issues in the approval process.
Similar forms
- Data Access Request Form: Similar in purpose, this document serves to request access to various databases that contain sensitive information, enabling organizations to manage and control who can access their data.
- User Access Request Form: This document is specifically designed for individual users to request permissions to use certain systems or applications, outlining their need for access and often requiring supervisor approval.
- IT Access Approval Form: This form is used to document the necessary approvals before granting a user access to IT systems, ensuring that the request aligns with security and privacy regulations.
- Confidentiality Agreement: Often required alongside access requests, this document helps ensure that users understand their responsibilities regarding the protection of sensitive data and outlines consequences for violations.
- System Access Request Form: Similar in function, this form is utilized to gain access to specific software systems, detailing the user’s role and justifying their request based on organizational needs.
- Authorization for Release of Information Form: This document requests permission to access or release sensitive information about individuals, often requiring informed consent from the data subjects.
- Data Sharing Agreement: Used when multiple parties collaborate, this agreement defines the terms under which data can be shared and sets expectations for data security and confidentiality.
- Workstation Access Request Form: This form requests permission to access a specific workstation or network, outlining the intended use and the user’s identification details for accountability.
Dos and Don'ts
When filling out the QIES Access Request form, it’s essential to follow some straightforward guidelines. Here’s a list of things you should and shouldn’t do:
- Do complete the form electronically to avoid any handwriting issues.
- Do ensure all sections are filled out completely, especially the user location and contact information.
- Do provide accurate and up-to-date information about your request and organization.
- Do sign the hard copy of the document in black or blue ink as required.
- Don’t share your identification number or password with anyone else.
- Don’t use CMS data files for any unauthorized or personal gain.
- Don’t alter or delete any CMS data unless you have explicit authorization.
- Don’t ignore the requirement for supervisor authorization; it’s required for approval.
Sticking to these dos and don’ts will help ensure that your request goes smoothly and complies with all necessary regulations.
Misconceptions
There are several misconceptions surrounding the QIES Access Request form that are important to clarify. Understanding the truth can greatly assist individuals and organizations in navigating the process effectively.
- Misconception 1: The form is only for new users.
- Misconception 2: Any employee can access sensitive data without authorization.
- Misconception 3: Supervisor and CMS authorization are optional.
- Misconception 4: The access request process is unnecessarily complicated.
- Misconception 5: Any user can share their identification number and password with colleagues.
Many believe that the QIES Access Request form is solely intended for individuals seeking a new User ID. In reality, the form accommodates various requests, such as changing access levels or deleting an existing User ID. It serves multiple purposes for managing user access within the CMS systems.
Some may think that being an employee is sufficient to gain access to sensitive data. However, it is crucial to understand that everyone must have explicit authorization, which requires proper completion of the form. Access is tightly controlled, as the information contains patient-level data that must be protected.
There is a belief that supervisor and CMS authorizations can be bypassed. This is incorrect. Both authorizations are required for the approval process. This ensures that requests are thoroughly reviewed and that access is granted only when it aligns with organizational needs and security protocols.
While the form may appear complex at first glance, its detailed nature ensures comprehensive security measures. By gathering essential information, the form helps facilitate a smooth access approval process while maintaining the integrity of sensitive data.
This misunderstanding can lead to serious security breaches. Identification numbers and passwords are unique to each user and must remain confidential. Sharing them violates security requirements and can lead to unauthorized access, with potential disciplinary consequences for the user involved.
Key takeaways
When filling out the QIES Access Request form, it is important to consider the following key takeaways:
- Complete the form electronically: It is essential to fill out the form electronically before printing it. This ensures clarity and correctness in the information provided.
- Specify the type of request: The form allows for requests to create a new user ID, change access, or delete a user ID. Make sure to select the appropriate option based on your needs.
- Include supervisor authorization: Approval from a supervisor is mandatory. Ensure that their name, phone number, and signature are included on the form to process your request.
- List the access needed: Clearly identify which types of access are required. This includes specific reports and data groups within the CMS systems.
- Understand security requirements: Familiarize yourself with the security protocols regarding the use of CMS data. It is critical to follow these guidelines to avoid potential penalties or legal consequences.
Browse Other Templates
Adp Flex Direct - Clarify any confusion regarding qualifying relatives or dependents with a qualified tax advisor.
Kink Checkbox - Curious about manacles and irons, values the element of play in their use.