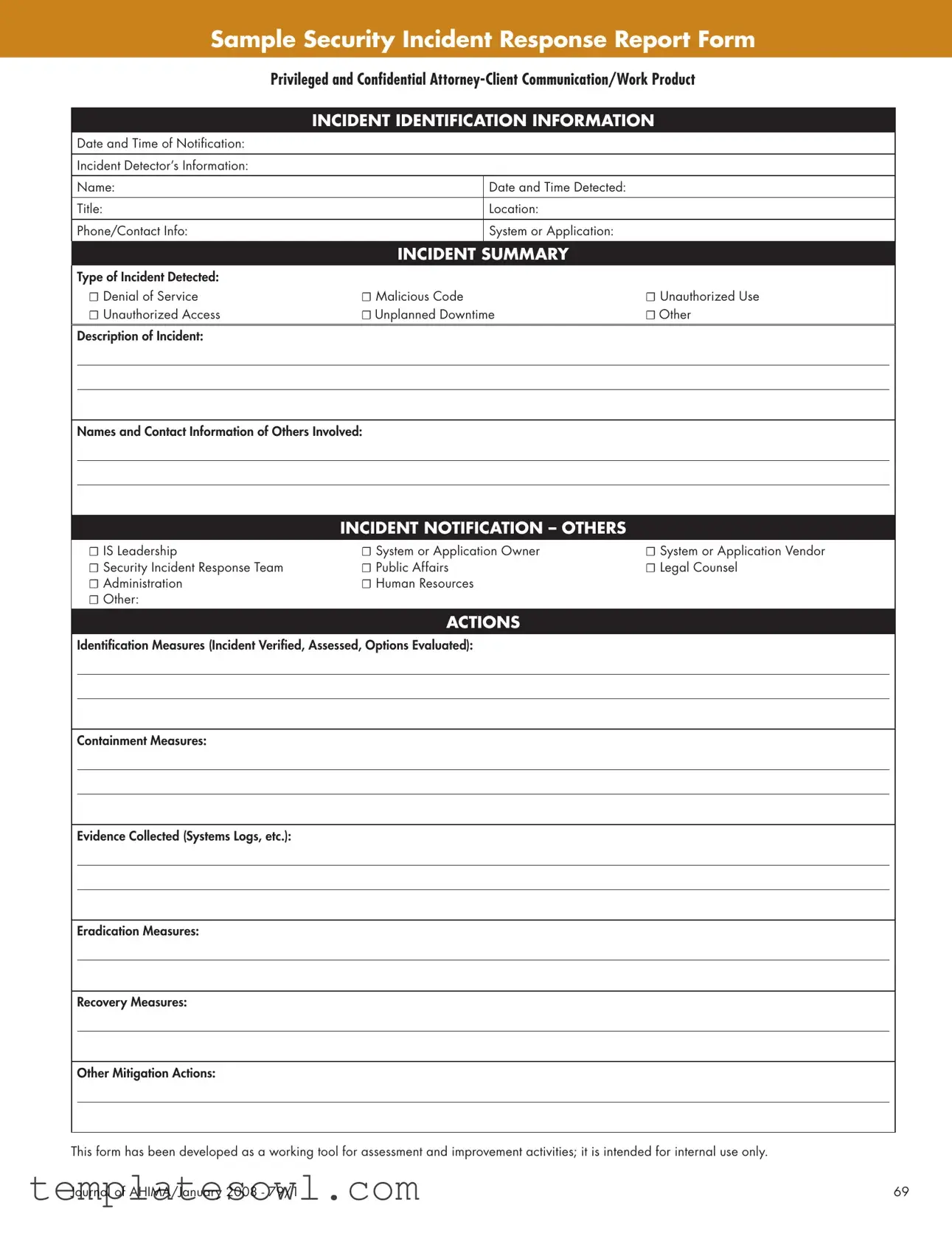
Fill Out Your Sample Security Incident Report Form
In the realm of modern security management, being prepared for incidents is crucial for any organization. The Sample Security Incident Report Form stands out as an essential tool to effectively document and respond to various types of security breaches. From unauthorized access to denial of service attacks, this form captures critical details that help guide the response process. It begins with fundamental incident identification information, such as the date and time of notification, the identity of the individual who detected the incident, and specifics regarding the involved system or application. Following this, a comprehensive summary of the incident itself is provided, allowing teams to categorize the type of incident and describe it in their own words. Not only does the form facilitate proper notification to necessary parties such as IS leadership and legal counsel, but it also includes a section dedicated to outlining the actions taken during the incident management process, covering everything from verification measures to evidence collection. Additionally, an evaluation section allows teams to reflect on their response, identify areas for improvement, and recommend actions to prevent future incidents. Through its structured yet flexible approach, this form acts as a valuable asset for organizations seeking to enhance both their incident response strategies and overall security posture.
Sample Security Incident Report Example

Sample Security Incident Response Report Form
Privileged and Confidential
INCIDENT IDENTIFICATION INFORMATION
Date and Time of Notification:
Incident Detector’s Information:
Name: |
Date and Time Detected: |
Title: |
Location: |
|
|
Phone/Contact Info: |
System or Application: |
|
|
INCIDENT SUMMARY
|
Type of Incident Detected: |
|
|
|
|
☐ Denial of Service |
☐ Malicious Code |
☐ Unauthorized Use |
|
|
☐ Unauthorized Access |
☐ Unplanned Downtime |
☐ Other |
|
|
|
|
|
|
|
Description of Incident: |
|
|
|
|
|
|
|
|
|
|
|
|
|
Names and Contact Information of Others Involved:
INCIDENT NOTIFICATION – OTHERS
☐ IS Leadership |
☐ System or Application Owner |
☐ System or Application Vendor |
☐ Security Incident Response Team |
☐ Public Affairs |
☐ Legal Counsel |
☐ Administration |
☐ Human Resources |
|
☐ Other: |
|
|
|
ACTIONS |
|
Identification Measures (Incident Verified, Assessed, Options Evaluated):
Containment Measures:
Evidence Collected (Systems Logs, etc.):
Eradication Measures:
Recovery Measures:
Other Mitigation Actions:
This form has been developed as a working tool for assessment and improvement activities; it is intended for internal use only.
Journal of AHIMA/January 2008 - 79/1 |
69 |
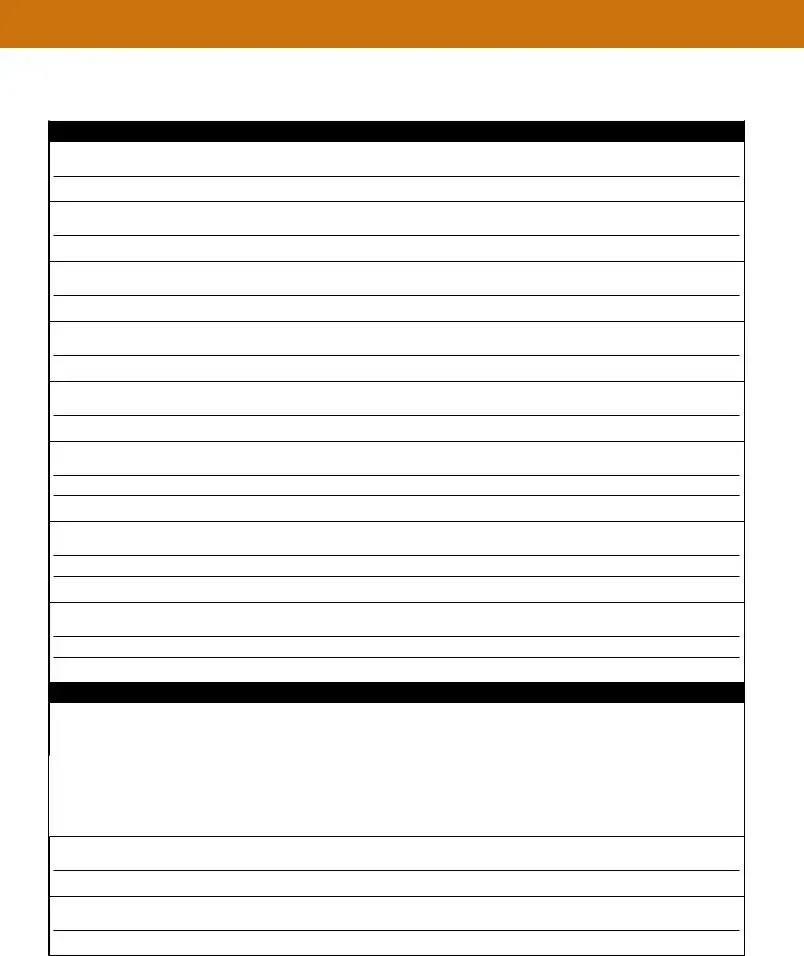
Sample Security Incident Response Report Form
Privileged and Confidential
EVALUATION
How Well Did Work Force Members Respond?
Were the Documented Procedures Followed? Were They Adequate?
What Information Was Needed Sooner?
Were Any Steps or Actions Taken That Might Have Inhibited the Recovery?
What Could Work Force Members Do Differently the Next Time an Incident Occurs?
What Corrective Actions Can Prevent Similar Incidents in the Future?
What Additional Resources Are Needed to Detect, Analyze, and Mitigate Future Incidents?
Other Conclusions or Recommendations:
|
|
||
|
Reviewed By: |
|
|
|
☐ Security Officer |
☐ IS Department/Team |
|
|
☐ Privacy Officer |
☐ Other |
|
|
|
|
|
|
Recommended Actions Carried Out: |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Initial Report Completed By:
This form has been developed as a working tool for assessment and improvement activities; it is intended for internal use only.
70 |
Journal of AHIMA/January 2008 - 79/1 |
Form Characteristics
| Fact Name | Description |
|---|---|
| Purpose | This form serves as a structured tool for documenting security incidents and assessing responses effectively. |
| Confidentiality | It is marked as privileged and confidential, emphasizing the sensitive nature of the information contained within. |
| Incident Types | The form includes various incident types such as Denial of Service, Malicious Code, and Unauthorized Access. |
| Evaluation Section | An evaluation section prompts reflection on the workforce response and the effectiveness of documented procedures. |
| Follow-Up | It requires a follow-up section to ensure that recommended actions are completed and reported properly. |
| Internal Use | The form is intended for internal use only, highlighting its role in improving incident management processes. |
Guidelines on Utilizing Sample Security Incident Report
Filling out the Sample Security Incident Report form can help ensure that all necessary details about the incident are documented. This form plays a crucial role in addressing security issues effectively. Gathering information accurately allows for a comprehensive response and helps prevent future incidents.
- Start with the INCIDENT IDENTIFICATION INFORMATION section. Fill in the Date and Time of Notification.
- Provide the Incident Detector’s Information:
- Name
- Date and Time Detected
- Title
- Location
- Phone/Contact Info
- System or Application
- Move to the INCIDENT SUMMARY section. Indicate the Type of Incident Detected by checking one of the options available.
- Provide a Description of Incident detailing what happened.
- List the Names and Contact Information of Others Involved in the incident.
- In the INCIDENT NOTIFICATION – OTHERS section, check off anyone who was notified about the incident.
- Next, describe the ACTIONS taken during the incident:
- Identification Measures
- Containment Measures
- Evidence Collected
- Eradication Measures
- Recovery Measures
- Other Mitigation Actions
- Proceed to the EVALUATION section. Answer the questions to assess the response to the incident.
- In the FOLLOW-UP section, fill in who reviewed the report and note any recommended actions that were carried out.
- Finally, include the Initial Report Completed By and Follow-Up Completed By sections to document who filled out the form.
What You Should Know About This Form
What is the purpose of the Sample Security Incident Report form?
The Sample Security Incident Report form serves as a structured tool to help organizations document and analyze security incidents. By collecting detailed information during an incident, it aids in improving response efforts and fostering a culture of security awareness.
Who needs to fill out this form?
This form should be completed by individuals who detect an incident, often in the IT or security teams. It may also involve collaboration with other relevant stakeholders such as system owners, legal counsel, and the security incident response team.
What types of incidents can be reported using this form?
The form is designed to report various types of incidents, including denial of service attacks, malicious code infections, unauthorized access, and unplanned downtimes. It can also cover other security-related issues, ensuring a comprehensive approach to incident management.
What information is needed to complete the form?
To fill out the form effectively, you will need details such as the date and time of notification, the incident type, a description of the incident, and the names and contact information of those involved. Collecting this information is crucial for accurate incident management.
What actions should be documented in the report?
The report should include identification measures, containment actions taken, evidence collected, eradication measures, and recovery efforts. Documenting these actions provides a clear picture of the response and helps identify areas for improvement.
How is the follow-up process handled?
After the initial report is created, it should be reviewed by designated individuals, such as the security officer or the privacy officer. Follow-up actions should also be documented, ensuring that any recommended improvements are clearly outlined and implemented.
Is the information in the report kept confidential?
Yes, the Sample Security Incident Report form is intended for internal use only and includes privileged and confidential information. Organizations should enforce strict access controls to protect sensitive data contained within the reports.
What should organizations do with the findings from this report?
Organizations should analyze the completed incident reports to identify patterns, assess response effectiveness, and implement corrective actions. Regularly reviewing findings helps bolster security measures and prevents similar incidents in the future.
Common mistakes
When filling out the Sample Security Incident Report form, many individuals make common mistakes that can lead to incomplete or inaccurate reporting. One frequent error occurs in the Incident Detector’s Information section. It is crucial for the name and contact information of the person who detected the incident to be filled in correctly. Omitting or miswriting this information can create confusion and hinder communication for follow-up actions.
Another common mistake is failing to provide a clear and detailed Description of Incident. This section is critical for understanding the nature of the incident. Vague language or jargon can complicate the incident's assessment. Take the time to articulate what happened so that everyone involved can have a clear understanding.
Individuals often neglect to select the appropriate Type of Incident Detected. This checkbox may seem trivial, but accurately categorizing the incident ensures proper attention and resources are allocated. Missing a type can lead to a mismanaged incident response, potentially exacerbating the situation.
Providing a comprehensive list of Names and Contact Information of Others Involved is often overlooked. Without this information, it may be difficult for the response team to gather crucial details from all parties related to the incident. Always include anyone who witnessed or was impacted by the incident.
Another issue arises in the ACTIONS section. Failing to document all Identification, Containment, and Recovery Measures taken can leave gaps in the incident response. Each action taken should be noted in detail to ensure a proper review and planning for future incidents.
Lastly, some individuals do not adequately complete the EVALUATION section. This part seeks to capture lessons learned from the incident. Skipping this could prevent improvements in procedures and responses for future incidents. Documenting what worked and what didn’t is necessary for ongoing preparedness.
Documents used along the form
When dealing with security incidents, having the right forms and documents in place is essential. Each document serves a specific purpose to streamline communication, evaluate response effectiveness, and ultimately enhance security measures. Here are some commonly used forms along with the Sample Security Incident Report form.
- Incident Response Plan: This document outlines the procedures for responding to various types of security incidents. It includes roles and responsibilities, communication strategies, and steps to restore security.
- Data Breach Notification Template: This template is used to inform affected individuals and regulatory bodies about a data breach. It ensures compliance with legal requirements and provides clear information to impacted parties.
- Evidence Collection Log: This log tracks the evidence collected during an incident investigation. It documents what was collected, who collected it, and when, ensuring a clear chain of custody.
- Risk Assessment Form: This form evaluates the potential risks associated with a particular security incident. It helps prioritize actions and allocate resources effectively based on the risk level identified.
- Post-Incident Review Report: This report analyzes the incident after it has been resolved. It examines responses, identifies what worked well, and recommends improvements for future incidents.
- Communication Plan: This is a strategic plan for how information will be communicated throughout an organization during and after an incident. It details who will speak to media, stakeholders, and employees.
- Incident Reporting Form: Similar to the Security Incident Report, this form enables employees to report suspicious activities or security breaches promptly. It ensures that all incidents are documented and investigated.
- Training Records: Maintaining records of employee training on security policies and incident response procedures is crucial. These records can be essential in demonstrating compliance and preparedness.
- Compliance Checklist: This checklist ensures that the organization meets relevant legal and regulatory standards related to data protection and security incident response.
Utilizing these documents in conjunction with the Sample Security Incident Report can enhance your organization's ability to respond effectively to security incidents. By preparing and organizing these forms, you can create a solid foundation for managing risks and improving security practices over time.
Similar forms
- Incident Report Form: Similar in structure, this document collects detailed information about security incidents. It typically includes sections for incident identification, description, and actions taken, much like the Sample Security Incident Report.
- Workplace Violence Report: This document also focuses on identifying and documenting incidents. It gathers information on the nature of the event, individuals involved, and actions taken, similar to the format of the security incident report.
- Data Breach Notification Template: Like the Sample Security Incident Report, this template is used to outline breaches, detailing when they occurred and who was affected. Both documents aim to ensure that all necessary parties are informed.
- Accident Report Form: This form is used to document workplace accidents. It shares a similar approach to capturing details about the incident, including the time, place, and individuals involved, just like the security incident report.
- Compliance Incident Report: Often used in regulated industries, this report captures compliance issues. Its focus on identifying the nature of incidents and outlining responses mirrors the layout of the security incident report.
- Health and Safety Incident Report: This document focuses on incidents related to health and safety in the workplace. It typically includes sections on the nature of the incident and responses taken, reflecting the approach of the security document.
- IT Service Outage Report: Similar in that it documents outages and their causes, this report shares a common format by listing incident details, affected systems, and recovery measures.
- Fraud Report Form: This document captures incidents of fraud. Just like the security incident report, it includes sections for describing the incident, affected parties, and the measures taken post-incident.
Dos and Don'ts
When filling out the Sample Security Incident Report form, certain practices can help ensure clarity and efficiency. Conversely, there are also habits to avoid that may complicate the process. Below is a list of guidelines to follow and to avoid.
- Do: Provide accurate and detailed information in all sections of the form.
- Do: Record the date and time of the incident as precisely as possible.
- Do: Include the names and contact details of all individuals involved in the incident.
- Do: Use clear language when describing the incident to help others understand the situation.
- Do: Follow the established procedures and guidelines for reporting incidents.
- Do: Ensure that any follow-up actions are noted and tracked accordingly.
- Do: Review the form with a colleague to verify that all necessary information has been included.
- Don't: Rush through the form; take your time to ensure that everything is complete.
- Don't: Leave any sections blank unless they are not applicable to the incident.
- Don't: Use vague language or abbreviations that could confuse the reader.
- Don't: Assume that someone else will fill in details you might forget; be thorough yourself.
- Don't: Discuss sensitive information outside of authorized personnel.
- Don't: Ignore the importance of documenting lessons learned for future reference.
- Don't: Submit the report without reviewing it for errors and completeness.
By adhering to these guidelines, the reporting process can be made more effective, fostering better communication and incident management.
Misconceptions
Misconceptions about the Sample Security Incident Report form can hinder effective use and understanding. Here are seven common misconceptions along with explanations:
- This form is only for major incidents. Many believe the report is unnecessary unless a significant security breach occurs. In reality, all incidents, regardless of size, should be documented to track patterns and improve future responses.
- Only IT personnel should fill out this report. This form is often seen as exclusive to IT staff. However, any employee who detects a potential incident can and should complete the form, ensuring a comprehensive response.
- The form is complex and time-consuming. Some may feel intimidated by the length and detail of the form. In truth, it is designed for clarity and efficiency, making it easier to gather crucial information swiftly.
- Filling out the form will lead to immediate consequences. Fear of repercussions may prevent individuals from reporting incidents. The form is intended for internal assessment and improvement, not for punitive measures against employees.
- All information collected is shared publicly. There is a concern that the information provided in the report will become public knowledge. However, the form is marked 'Privileged and Confidential,' ensuring its use remains strictly internal.
- The report is only useful during investigations. Some individuals only view the report's value during a security investigation. Conversely, this form serves a proactive role by helping improve processes and training for future incidents.
- This form does not contribute to overall security policies. A belief exists that using the report has no broader impact on security strategies. In reality, the accumulated data from various reports helps organizations identify trends and enhance their security measures.
Clarifying these misconceptions fosters a better understanding of the Sample Security Incident Report form's importance in maintaining a secure environment.
Key takeaways
Accurate and detailed information is crucial. When filling out the Sample Security Incident Report form, ensure that all sections, particularly incident detection details and system or application specifics, are filled out thoroughly.
Response evaluation is an essential ongoing process. After completing the report, assess how well the team responded to the incident and whether procedures were adequate.
Engaging appropriate parties is vital. Notify all relevant stakeholders, such as the Security Incident Response Team and legal counsel, as indicated in the 'Incident Notification' section of the form.
Mitigation should be comprehensive. Document all actions taken, including identification, containment, and recovery measures, to provide a clear record of how the incident was managed.
Use the form for improvement. Post-incident evaluations can yield insights into how to bolster procedures and prevent future occurrences.
Browse Other Templates
Intent to Purchase Letter - Specific details of the personal property can be detailed in an attached list if needed.
Wells Fargo Beneficiary Form - Engage with Wells Fargo’s services related to subordination by utilizing this essential form.